Course: Microsoft Azure Security Technologies: Data Classification (exam AZ-500)
As low as
duration: 19 hours |
Language: English (US) |
access duration: 180 days |

Details
Are you planning to become a Microsoft Certified: Azure Security engineer Associate? In this training, you will be prepared for the AZ-500 exam.
In this training you build the required knowledge and skills to implement security controls, you learn how you can continue to maintain your security status and how you identify system attacks, but you also repair them using the various security tools.
Finally, scripting and automation are treated as well as virtualization and cloud N-tier architecture.
Result
After successful completion of this training:
- You can describe specialized data classifications on Azure.
- You can Identify Azure data protection mechanisms
- You can Implement azure data encryption methods.
- You know how to implement secure internet protocols on Azure.
- You can describe your Azure security services and functions.
- You can identify Azure data protection mechanisms.
Finally, you are optimally prepared for the AZ-500 exam. After passing the AZ-500 exam you will obtain the Microsoft Certified: Azure Security engineer Associate certification.
Prerequisites
You have at least one year of practical experience with securing Azure work and experience with security controls for work with Azure.
Target audience
System Administrator, Network Administrator, Database Administrators
Content
Microsoft Azure Security Technologies: Data Classification (exam AZ-500)
AZ-500 - Microsoft Azure Security Technologies: Azure Storage Account Security
AZ-500 - Microsoft Azure Security Technologies: Data Classification
AZ-500 - Microsoft Azure Security Technologies: Database Security
Explore how to secure your SQL and NoSQL Azure deployments through encryption, data masking, geo-fencing, and backups. Examine database auditing and how it can be used to shed light on security violations. This course can be used in preparation for the AZ-500 Microsoft Azure Security Technologies certification exam.
AZ-500 - Microsoft Azure Security Technologies: Database User Access
Explore how SQL and Azure AD logins can be used to authenticate
- to Azure SQL deployments and how RBAC and the Azure SQL Firewall
- also control database access. Discover how TDE provides data
- confidentiality and how security can be enhanced with database
- vulnerability assessments and threat policies. This course can be
- used in preparation for the AZ-500 Microsoft Azure Security
- Technologies certification exam.
AZ-500 - Microsoft Azure Security Technologies: Identity & Access Management
Discover how Azure AD can be used as a central identity provider
- to control resource access and how AD tenants can be created for
- identity isolation. Explore how access reviews can shed light on
- permissions that are no longer required and how Azure AD
- conditional access can secure Azure AD authentication through
- conditional access policies and OAuth 2.0. This course can be used
- in preparation for the AZ-500 Microsoft Azure Security Technologies
- certification exam.
AZ-500 - Microsoft Azure Security Technologies: Azure AD Connect
Discover how Azure AD Connect can link on-premises AD
- installations with Azure AD and how SSO can remove the need for
- users to authenticate to each and every app. Explore how to
- troubleshoot AD Connect sync issues with the Azure AD Connect
- troubleshooting tool. This course can be used in preparation for
- the AZ-500 Microsoft Azure Security Technologies certification
- exam.
AZ-500 - Microsoft Azure Security Technologies: Azure AD User Management
Explore the many ways Azure AD users can be created using bulk
- file import and how to enable MFA for some or all Azure AD users to
- enhance user sign-in security. Discover how SSPR allows users to
- reset their own forgotten passwords and how password lockout
- settings prevent brute-force attacks against Azure AD user
- accounts. This course can be used in preparation for the AZ-500
- Microsoft Azure Security Technologies certification exam.
AZ-500 - Microsoft Azure Security Technologies: Azure AD Group Management
Explore methods for managing Azure Active Directory groups,
- including how static groups have a manually configured membership
- and dynamic groups determine membership based on attributes.
- Discover how SSGM allows users to request group membership and
- group owners to control membership. This course can be used in
- preparation for the AZ-500 Microsoft Azure Security Technologies
- certification exam.
AZ-500 - Microsoft Azure Security Technologies: Network Security
Discover how VNets can be used to isolate Azure cloud resources
- and how NSGs can allow or deny traffic to or from subnets and VM
- network interfaces. Examine the use of SSH for managing Linux, RDP
- for managing Windows, and jump boxes as central, publicly
- accessible administrative points. In addition, explore how Azure
- Firewall supports different types of rules to control network
- traffic into and out of networks. This course can be used in
- preparation for the AZ-500 Microsoft Azure Security Technologies
- certification exam.
AZ-500 - Microsoft Azure Security Technologies: VPNs
AZ-500 - Microsoft Azure Security Technologies: Web Application Security
Discover how the design and implementation of a web app in the
- Azure cloud can determine its security posture. Explore how using
- custom domain names with TLS bindings allows the use of a custom
- DNS domain with connectivity over HTTPS and how web apps can also
- be backed up and protected by a WAF. Examine how API Gateways serve
- as proxies between the calling of an API and the API itself and how
- Application Security Groups organize and protect VMs based on their
- running workloads. This course can be used in preparation for the
- AZ-500 Microsoft Azure Security Technologies certification
- exam.
AZ-500 - Microsoft Azure Security Technologies: Application Containers
Discover how application containers isolate app files and
- settings from the OS and other apps. Explore how containers can be
- secured in similar ways to app workloads, including how to apply
- updates and provide limited access. This course can be used in
- preparation for the AZ-500 Microsoft Azure Security Technologies
- certification exam.
AZ-500 - Microsoft Azure Security Technologies: Azure Key Vault
Explore Azure key vaults and how they can contain secrets, keys,
- and certificates, which are used to secure other resources such as
- VM disks and databases. Examine the key vault access policy and how
- it controls access to key vault contents. This course can be used
- in preparation for the AZ-500 Microsoft Azure Security Technologies
- certification exam.
AZ-500 - Microsoft Azure Security Technologies: Azure RBAC & Policies
Discover how to use RBAC to limit administrative access to Azure
- resources at the subscription, resource group, and resource levels.
- Explore how Azure policies provide more granularity than RBAC for
- the deployment and management of Azure resources. This course can
- be used in preparation for the AZ-500 Microsoft Azure Security
- Technologies certification exam.
AZ-500 - Microsoft Azure Security Technologies: Monitoring, Logging, & Alerts
Discover how to use Log Analytic workspaces to centralize Azure
- resource logged data from a variety of sources and how to run log
- queries. Examine how to configure Azure Monitor centralized alert
- and notification settings. This course can be used in preparation
- for the AZ-500 Microsoft Azure Security Technologies certification
- exam.
AZ-500 - Microsoft Azure Security Technologies: Azure Security Center
Explore the Azure Security Center and discover how it
- automatically collects Azure resource security metrics and provides
- hardening recommendations. Examine how playbooks can remediate
- security issues and can be triggered by alerts. This course can be
- used in preparation for the AZ-500 Microsoft Azure Security
- Technologies certification exam.
AZ-500 - Microsoft Azure Security Technologies: Review Course 1
Security must be considered when designing, implementing,
- managing, and monitoring Microsoft Azure usage. Review core
- concepts including how to apply security for Azure storage
- solutions ranging from storage accounts to Azure SQL Database.
- Specifically, review how to secure storage accounts, organize cloud
- resources with tagging, enable database masking, and configure
- Azure SQL firewall. This course can be used in preparation for the
- AZ-500 Microsoft Azure Security Technologies certification
- exam.
AZ-500 - Microsoft Azure Security Technologies: Review Course 2
Review core concepts of Azure security, including how to apply
- security for a variety of Azure network and virtual machine
- solutions. Refresh your knowledge on how RBAC is used to delegate
- administrative access, and how to view Azure Security Center
- recommendations. Remind yourself on how to enable multi-factor
- authentication, password lockout, site-to-site connectivity, and
- JIT for VMs. In addition, review how to create a network security
- group, limit resource access, and use Azure Security Center. This
- course can be used in preparation for the AZ-500 Microsoft Azure
- Security Technologies certification exam.
Course options
We offer several optional training products to enhance your learning experience. If you are planning to use our training course in preperation for an official exam then whe highly recommend using these optional training products to ensure an optimal learning experience. Sometimes there is only a practice exam or/and practice lab available.
Optional practice exam (trial exam)
To supplement this training course you may add a special practice exam. This practice exam comprises a number of trial exams which are very similar to the real exam, both in terms of form and content. This is the ultimate way to test whether you are ready for the exam.
Optional practice lab
To supplement this training course you may add a special practice lab. You perform the tasks on real hardware and/or software applicable to your Lab. The labs are fully hosted in our cloud. The only thing you need to use our practice labs is a web browser. In the LiveLab environment you will find exercises which you can start immediately. The lab enviromentconsist of complete networks containing for example, clients, servers,etc. This is the ultimate way to gain extensive hands-on experience.
Sign In
WHY_ICTTRAININGEN
Via ons opleidingsconcept bespaar je tot 80% op trainingen
Start met leren wanneer je wilt. Je bepaalt zelf het gewenste tempo
Spar met medecursisten en profileer je als autoriteit in je vakgebied.
Ontvang na succesvolle afronding van je cursus het officiële certificaat van deelname van Icttrainingen.nl
Krijg inzicht in uitgebreide voortgangsinformatie van jezelf of je medewerkers
Kennis opdoen met interactieve e-learning en uitgebreide praktijkopdrachten door gecertificeerde docenten
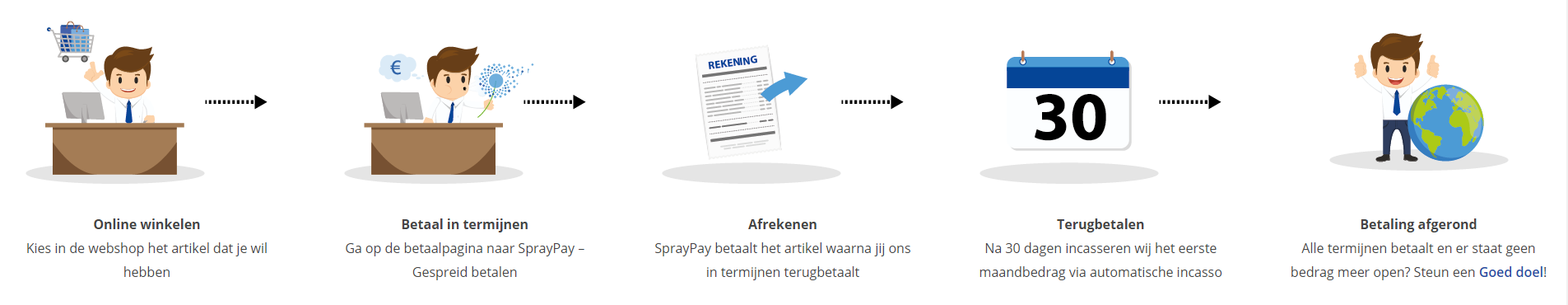
Orderproces
Once we have processed your order and payment, we will give you access to your courses. If you still have any questions about our ordering process, please refer to the button below.
read more about the order process
Een zakelijk account aanmaken
Wanneer u besteld namens uw bedrijf doet u er goed aan om aan zakelijk account bij ons aan te maken. Tijdens het registratieproces kunt u hiervoor kiezen. U heeft vervolgens de mogelijkheden om de bedrijfsgegevens in te voeren, een referentie en een afwijkend factuuradres toe te voegen.
Betaalmogelijkheden
U heeft bij ons diverse betaalmogelijkheden. Bij alle betaalopties ontvangt u sowieso een factuur na de bestelling. Gaat uw werkgever betalen, dan kiest u voor betaling per factuur.

Cursisten aanmaken
Als u een zakelijk account heeft aangemaakt dan heeft u de optie om cursisten/medewerkers aan te maken onder uw account. Als u dus meerdere trainingen koopt, kunt u cursisten aanmaken en deze vervolgens uitdelen aan uw collega’s. De cursisten krijgen een e-mail met inloggegevens wanneer zij worden aangemaakt en wanneer zij een training hebben gekregen.
Voortgangsinformatie
Met een zakelijk account bent u automatisch beheerder van uw organisatie en kunt u naast cursisten ook managers aanmaken. Beheerders en managers kunnen tevens voortgang inzien van alle cursisten binnen uw organisatie.
What is included?
| Certificate of participation | Yes |
| Monitor Progress | Yes |
| Award Winning E-learning | Yes |
| Mobile ready | Yes |
| Sharing knowledge | Unlimited access to our IT professionals community |
| Study advice | Our consultants are here for you to advice about your study career and options |
| Study materials | Certified teachers with in depth knowledge about the subject. |
| Service | World's best service |
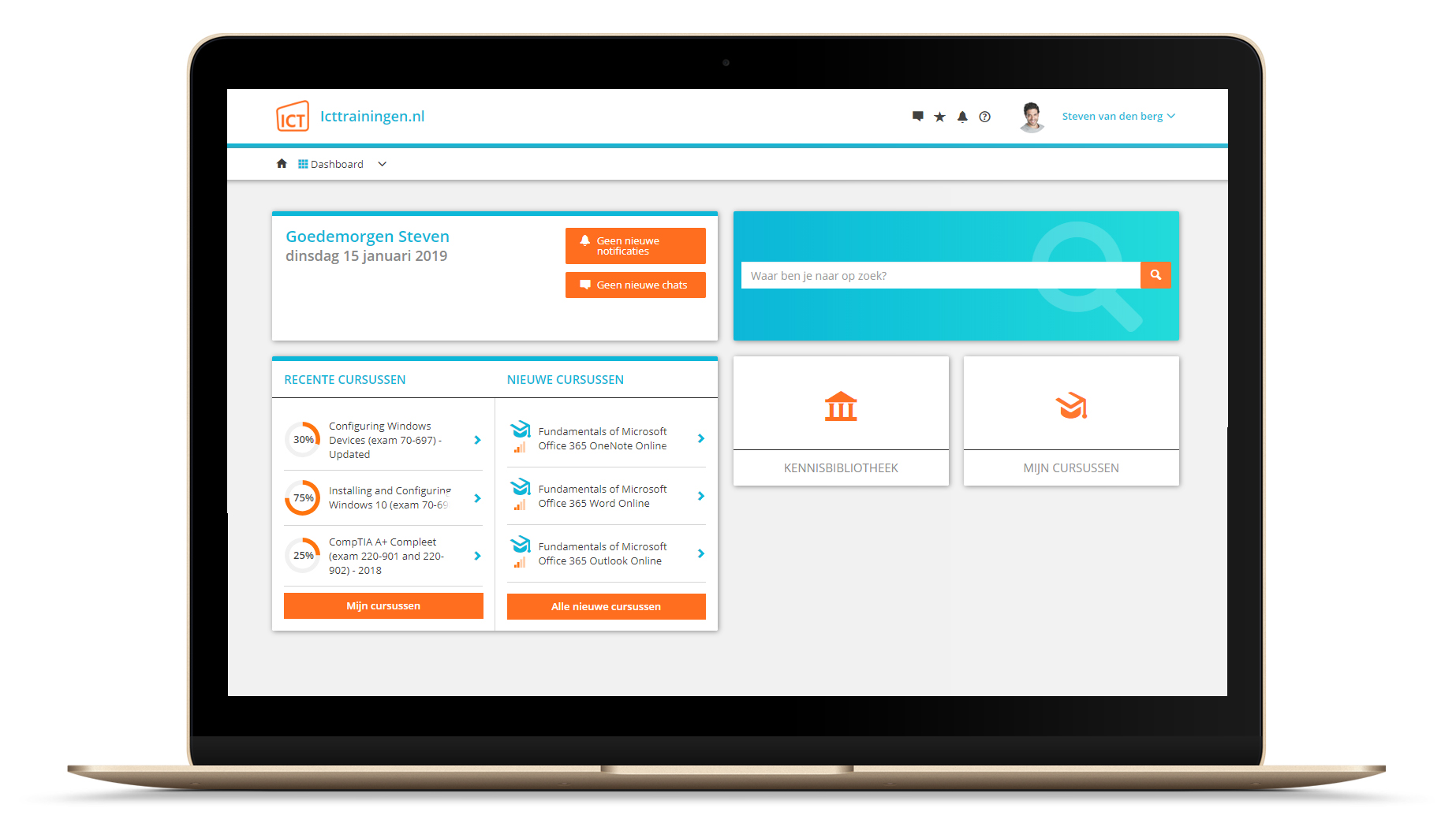
Platform
Na bestelling van je training krijg je toegang tot ons innovatieve leerplatform. Hier vind je al je gekochte (of gevolgde) trainingen, kan je eventueel cursisten aanmaken en krijg je toegang tot uitgebreide voortgangsinformatie.
FAQ
Niet gevonden wat je zocht? Bekijk alle vragen of neem contact op.