Course: Windows Exploits and Forensics
duration: 12 hours |
Language: English (US) |
access duration: 90 days |

Details
As a security operations person, you'll need to employ various Windows exploitation techniques to attack vulnerable target software and services. In this course, you will learn how to use this.
You will discover the various intelligence gathering techniques used for conducting offensive security operations against a Windows-based network to identify possible vulnerabilities. Next you learn about some core competencies required to conduct offensive security operations against a Windows environment. To know what kind of attacks, exploits, and vulnerabilities to look out for, you get to know the most common services used to attack a Windows-based network - SMB and PsExec - along with some popular attack methodologies. To protect an operating system, you must first know how to exploit it. Therefore, you learn about some of the standard Windows services that have known exploits available for them, which can be used in offensive security operations against a Windows environment. The use of systems that are no longer serviced and supported and therefore, do not receive security updates, exposes an organization to serious security attacks. To ensure a healthy network ecosystem, you'll explore how to conduct offensive security operations against legacy Windows-based systems. Finally, you’ll learn to recognize common post exploitation activities within a Windows environment and how to configure an advanced persistent threat.
Result
After successfully completing this course, you can use various Windows exploitation techniques to attack vulnerable target software and services.
Prerequisites
Some experience in security operations is recommended.
Target audience
Security Specialist
Content
Windows Exploits and Forensics
Windows Exploits and Forensics: Intelligence Gathering
As a security operations person, you'll need to employ various Windows exploitation techniques to attack vulnerable target software and services. This course covers the various intelligence gathering techniques used for conducting offensive security operations against a Windows-based network to identify possible vulnerabilities.
You'll start by examining open source intelligence (OSINT) gathering techniques and sources before conducting your own OSINT investigation. Next, you'll explore the use of social media and other tools for finding targets for social engineering exercises. You'll then examine common Windows services and their ports and tools for conducting basic enumeration.
Moving along, you'll practice network scanning for open ports, scanning a Windows-based system, and enumerating data. Lastly, you'll explore various tools used in the Kali hacking environment, the use of Metasploitable, and common locations to find Windows exploits.
Windows Exploits and Forensics : Windows Environments
As a security operations person, you'll need to tailor your methods to suit the operating system your working with. This course covers some of the core competencies required to conduct offensive security operations against a Windows environment.
Throughout this course, you'll learn how to recognize the differences between various Windows versions. You'll examine the role of intrusion detection systems (IDS) and intrusion prevention systems (IPS) in a Windows environment. You'll then learn about the MITRE ATT&CK framework and how it relates to Windows intrusions and identify the different Windows logging mechanisms.
Next, you'll practice using event logging, basic PowerShell commands, and the Windows Registry. You'll then explore how the Windows hashing algorithm works and practice cracking an NTLM hash value. Lastly, you'll investigate different data artifacts within Windows and outline how best to work with Active Directory and Kerberos.
Windows Exploits and Forensics: SMB & PsExec
When carrying out security operations in a Windows environment, you need to know what kind of attacks, exploits, and vulnerabilities to look out for. This course covers two of the most common services used to attack a Windows-based network - SMB and PsExec - along with some popular attack methodologies.
You'll start by examining SMB permissions and default settings. You'll then explore tools to enumerate SMB shares and data. Next, you'll investigate how to identify SMB vulnerabilities and recognize SMB attacks. You'll then conduct different SMB exploits, including brute force and denial of service attacks.
You'll move on to outline how PsExec works and use it to execute remote commands. Finally, you'll practice exploiting PsExec using various tools, including the EternalBlue exploit.
Windows Exploits and Forensics: FTP, RDP, & Other Services
To protect an operating system, you must first know how to exploit it. This course covers some of the standard Windows services that have known exploits available for them, which can be used in offensive security operations against a Windows environment.
You'll start by enumerating data from a Windows-based FTP server before practicing methods used to attack FTP services. You'll then learn how to attack IIS-based systems. Next, you'll examine the RPD protocol and learn methods of attacking the Windows RDP service. Finally, you'll investigate how WMI works and learn to exploit WMI on a Windows-based machine.
This course involves conducting brute force attacks, reverse shells, and using the BlueKeep security vulnerability.
Windows Exploits and Forensics: Legacy Systems & Third Party Applications
When an organization uses systems that are no longer serviced and supported and therefore, do not receive security updates, they expose themselves to serious security attacks. To ensure a healthy network ecosystem, security operations personnel must be aware of the vulnerabilities these systems are exposed to.
In this course, you'll explore how to conduct offensive security operations against legacy Windows-based systems. You'll learn to recognize older versions of Windows, identify common exploits for these older versions, and scan Server 2008 for vulnerabilities. You'll then learn how to enumerate Server 2008, exploit legacy systems, and gain a reverse shell on a legacy system. You'll then learn how to recognize common third-party applications and vulnerabilities and how to exploit them. Finally, you'll learn how to identify and avoid a honeypot.
Windows Exploits and Forensics: Post Exploitation
As a penetration tester, it's vital that you are familiar with
- advanced methods of conducting offensive security operations
- against Windows environments. In this course, you’ll learn to
- recognize common post exploitation activities within a Windows
- environment and how to configure an advanced persistent threat.
- You’ll start by learning how to escalate privileges, use a DLL
- injection attack, pivot between systems, and crack user
- credentials. You'll then examine how to use PowerView to enumerate
- information and use BloodHound to 'walk the dog' and gain domain
- admin privileges. Finally, you'll learn how to clean up post attack
- to cover your tracks, create an advanced persistent threat, and use
- a ransomware attack to lock a system.
Course options
We offer several optional training products to enhance your learning experience. If you are planning to use our training course in preperation for an official exam then whe highly recommend using these optional training products to ensure an optimal learning experience. Sometimes there is only a practice exam or/and practice lab available.
Optional practice exam (trial exam)
To supplement this training course you may add a special practice exam. This practice exam comprises a number of trial exams which are very similar to the real exam, both in terms of form and content. This is the ultimate way to test whether you are ready for the exam.
Optional practice lab
To supplement this training course you may add a special practice lab. You perform the tasks on real hardware and/or software applicable to your Lab. The labs are fully hosted in our cloud. The only thing you need to use our practice labs is a web browser. In the LiveLab environment you will find exercises which you can start immediately. The lab enviromentconsist of complete networks containing for example, clients, servers,etc. This is the ultimate way to gain extensive hands-on experience.
Sign In
WHY_ICTTRAININGEN
Via ons opleidingsconcept bespaar je tot 80% op trainingen
Start met leren wanneer je wilt. Je bepaalt zelf het gewenste tempo
Spar met medecursisten en profileer je als autoriteit in je vakgebied.
Ontvang na succesvolle afronding van je cursus het officiële certificaat van deelname van Icttrainingen.nl
Krijg inzicht in uitgebreide voortgangsinformatie van jezelf of je medewerkers
Kennis opdoen met interactieve e-learning en uitgebreide praktijkopdrachten door gecertificeerde docenten
Orderproces
Once we have processed your order and payment, we will give you access to your courses. If you still have any questions about our ordering process, please refer to the button below.
read more about the order process
Een zakelijk account aanmaken
Wanneer u besteld namens uw bedrijf doet u er goed aan om aan zakelijk account bij ons aan te maken. Tijdens het registratieproces kunt u hiervoor kiezen. U heeft vervolgens de mogelijkheden om de bedrijfsgegevens in te voeren, een referentie en een afwijkend factuuradres toe te voegen.
Betaalmogelijkheden
U heeft bij ons diverse betaalmogelijkheden. Bij alle betaalopties ontvangt u sowieso een factuur na de bestelling. Gaat uw werkgever betalen, dan kiest u voor betaling per factuur.

Cursisten aanmaken
Als u een zakelijk account heeft aangemaakt dan heeft u de optie om cursisten/medewerkers aan te maken onder uw account. Als u dus meerdere trainingen koopt, kunt u cursisten aanmaken en deze vervolgens uitdelen aan uw collega’s. De cursisten krijgen een e-mail met inloggegevens wanneer zij worden aangemaakt en wanneer zij een training hebben gekregen.
Voortgangsinformatie
Met een zakelijk account bent u automatisch beheerder van uw organisatie en kunt u naast cursisten ook managers aanmaken. Beheerders en managers kunnen tevens voortgang inzien van alle cursisten binnen uw organisatie.
What is included?
| Certificate of participation | Yes |
| Monitor Progress | Yes |
| Award Winning E-learning | Yes |
| Mobile ready | Yes |
| Sharing knowledge | Unlimited access to our IT professionals community |
| Study advice | Our consultants are here for you to advice about your study career and options |
| Study materials | Certified teachers with in depth knowledge about the subject. |
| Service | World's best service |
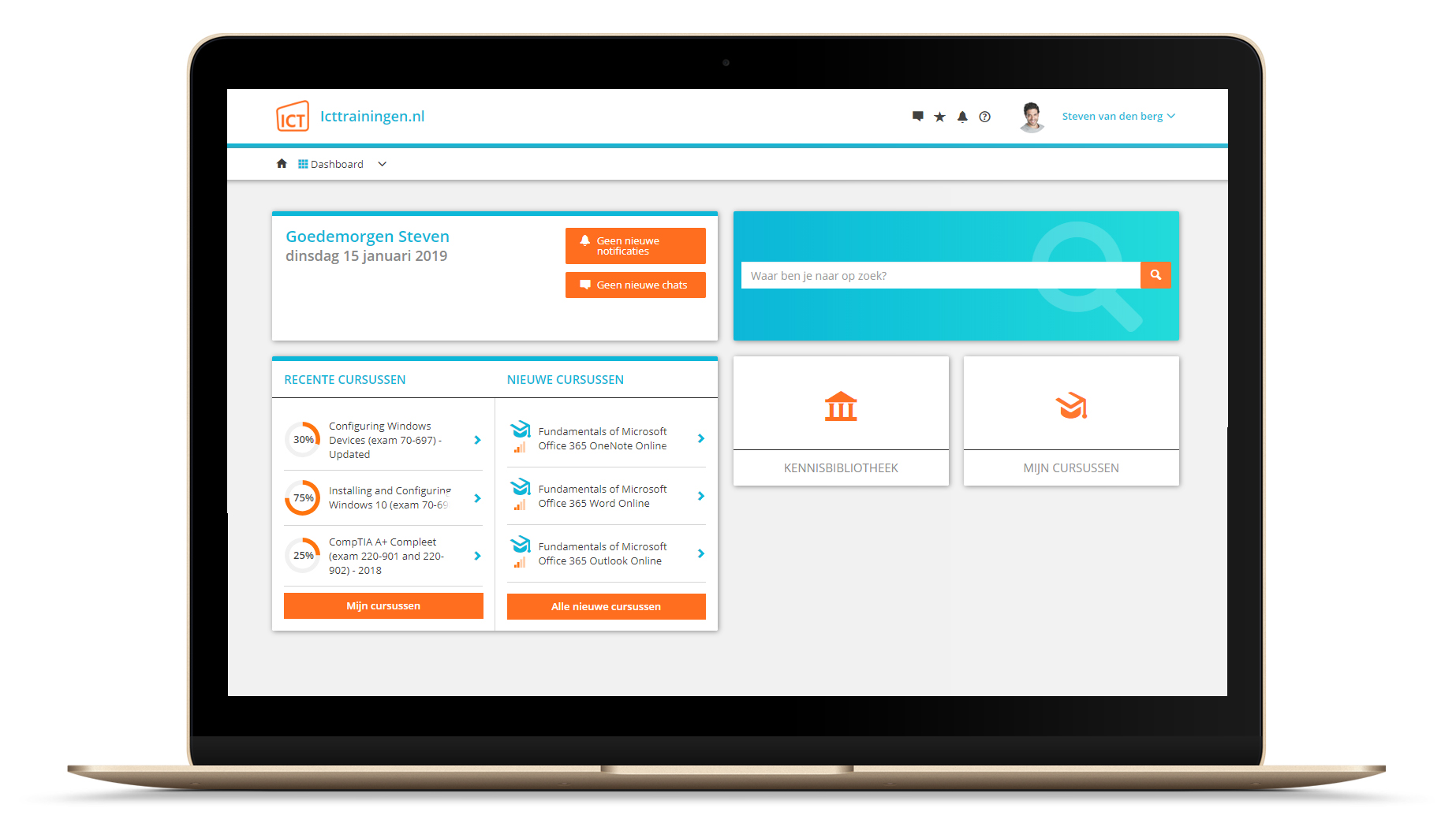
Platform
Na bestelling van je training krijg je toegang tot ons innovatieve leerplatform. Hier vind je al je gekochte (of gevolgde) trainingen, kan je eventueel cursisten aanmaken en krijg je toegang tot uitgebreide voortgangsinformatie.
FAQ
Niet gevonden wat je zocht? Bekijk alle vragen of neem contact op.