Security Analyst to Security Architect- Track 2 Forensics Analyst
duration: 14 hours |
Language: English (US) |
access duration: 365 days |

Details
This is the second track of the learning path Security Analyst to Security Architect. The focus in this track is on the role of Forensic Analyst.
The emphasis is on your awareness as an end-user, anomaly detection, digital forensics, digital ethics and privacy, risk analysis, software assessment & audits, and cryptography.
In this track of the learning path you will find various training courses that prepare you to get started as a Forensic Analyst. In addition, a live lab is available that teaches you to apply the learned theory in a practical environment. You conclude this part with an exam.
Result
After completing this track, you will have the knowledge and skills to work as a Forensic Analyst. You are ready to get started with track 3 of this learning path.
Prerequisites
You are expected to master the knowledge and skills that are covered in track 1 (Security Analyst) of this learning path.
Target audience
Security Specialist
Content
Security Analyst to Security Architect- Track 2 Forensics Analyst
End-User Security: The End-User Perspective
Examine end-user security concepts such as shared responsibilities and policies, physical controls, authentication, software, and best practices.
End-User Security: The Security Administrator Perspective
Examine end-user security from the security administrator point-of-view including threatscape, security policies, training and awareness, Layer 2 security, 802.1X, MACsec, EDR, advanced endpoint protection, and vendor solutions.
End-User Security: Securing End Users against Attackers
Examine end-user security from the rogue attacker point-of-view including motivations, MaaS, phishing techniques, ransomware, data theft, cryptojacking, DoS, and toolkits.
Anomaly Detection: Aspects of Anomaly Detection
Network anomalies are behaviors or activities that deviate from
- the norm. It is important that security professionals learn to
- monitor for these anomalies in network traffic because the traffic
- could be malicious traffic. Explore the role network and security
- professionals play in detecting and addressing anomalies,
- determining if anomalies are malicious, and best practices in
- monitoring and detection.
Anomaly Detection: Network Anomaly Detection
Explore best practices for anomaly detection for network forensics with topics such as network behavior anomaly detection, frequency analysis, identifying beaconing activity, and recognizing the signs of a brute force attack. Also discover protocal and popluation analysis, HTTPS and SSH attacks, as well as triage methods.
Digital Forensic Techniques & Investigative Approaches
Digital Forensic Techniques & Investigative Approaches
Ethics & Privacy: Digital Forensics
Risk Analysis: Security Risk Management
Explore security risk management concepts and discover how to assess, categorize, monitor, and respond to organizational risks. Examine key terms such as threats, vulnerabilities, impacts, and risks, as well as the steps involved in the NIST risk management framework.
Cryptography: Introduction to Cryptography Services
Cryptography: Introduction to PKI
Forensics Analyst
- Practice Forensics Analyst tasks such as implementing web browser best practices, preventing brute force attacks, installing SIFT and detecting and removing keylogger software. Then, test your skills by answering assessment questions after auditing network security, applying Caesar cipher encryption techniques, implementing secure coding techniques and symmetric encryption.
- This lab provides access to tools typically by Forensics Analysts, including:
- � PowerShell 5.1
- � Windows Defender
- � Revealer Keylogger
- � Wireshark
- � Cryptool
- � Visual Studio Code
- � Java Runtime
- � Oracle VM VirtualBox
- This lab is part of the Forensics Analyst track of the Skillsoft Aspire Security Analyst to Security Architect journey.
Final Exam: Forensics Analyst
Final Exam: Forensics Analyst will test your knowledge and application of the topics presented throughout the Forensics Analyst track of the Skillsoft Aspire Security Analyst to Security Architect Journey. Learners seeking to test their knowledge and application of Forensics Analyst skills and those seeking to complete the Forensics Analyst track of the Skillsoft Aspire Security Analyst to Security Architect Journey.
Course options
We offer several optional training products to enhance your learning experience. If you are planning to use our training course in preperation for an official exam then whe highly recommend using these optional training products to ensure an optimal learning experience. Sometimes there is only a practice exam or/and practice lab available.
Optional practice exam (trial exam)
To supplement this training course you may add a special practice exam. This practice exam comprises a number of trial exams which are very similar to the real exam, both in terms of form and content. This is the ultimate way to test whether you are ready for the exam.
Optional practice lab
To supplement this training course you may add a special practice lab. You perform the tasks on real hardware and/or software applicable to your Lab. The labs are fully hosted in our cloud. The only thing you need to use our practice labs is a web browser. In the LiveLab environment you will find exercises which you can start immediately. The lab enviromentconsist of complete networks containing for example, clients, servers,etc. This is the ultimate way to gain extensive hands-on experience.
Sign In
WHY_ICTTRAININGEN
Via ons opleidingsconcept bespaar je tot 80% op trainingen
Start met leren wanneer je wilt. Je bepaalt zelf het gewenste tempo
Spar met medecursisten en profileer je als autoriteit in je vakgebied.
Ontvang na succesvolle afronding van je cursus het officiële certificaat van deelname van Icttrainingen.nl
Krijg inzicht in uitgebreide voortgangsinformatie van jezelf of je medewerkers
Kennis opdoen met interactieve e-learning en uitgebreide praktijkopdrachten door gecertificeerde docenten
Orderproces
Once we have processed your order and payment, we will give you access to your courses. If you still have any questions about our ordering process, please refer to the button below.
read more about the order process
Een zakelijk account aanmaken
Wanneer u besteld namens uw bedrijf doet u er goed aan om aan zakelijk account bij ons aan te maken. Tijdens het registratieproces kunt u hiervoor kiezen. U heeft vervolgens de mogelijkheden om de bedrijfsgegevens in te voeren, een referentie en een afwijkend factuuradres toe te voegen.
Betaalmogelijkheden
U heeft bij ons diverse betaalmogelijkheden. Bij alle betaalopties ontvangt u sowieso een factuur na de bestelling. Gaat uw werkgever betalen, dan kiest u voor betaling per factuur.

Cursisten aanmaken
Als u een zakelijk account heeft aangemaakt dan heeft u de optie om cursisten/medewerkers aan te maken onder uw account. Als u dus meerdere trainingen koopt, kunt u cursisten aanmaken en deze vervolgens uitdelen aan uw collega’s. De cursisten krijgen een e-mail met inloggegevens wanneer zij worden aangemaakt en wanneer zij een training hebben gekregen.
Voortgangsinformatie
Met een zakelijk account bent u automatisch beheerder van uw organisatie en kunt u naast cursisten ook managers aanmaken. Beheerders en managers kunnen tevens voortgang inzien van alle cursisten binnen uw organisatie.
What is included?
| Certificate of participation | Yes |
| Monitor Progress | Yes |
| Award Winning E-learning | Yes |
| Mobile ready | Yes |
| Sharing knowledge | Unlimited access to our IT professionals community |
| Study advice | Our consultants are here for you to advice about your study career and options |
| Study materials | Certified teachers with in depth knowledge about the subject. |
| Service | World's best service |
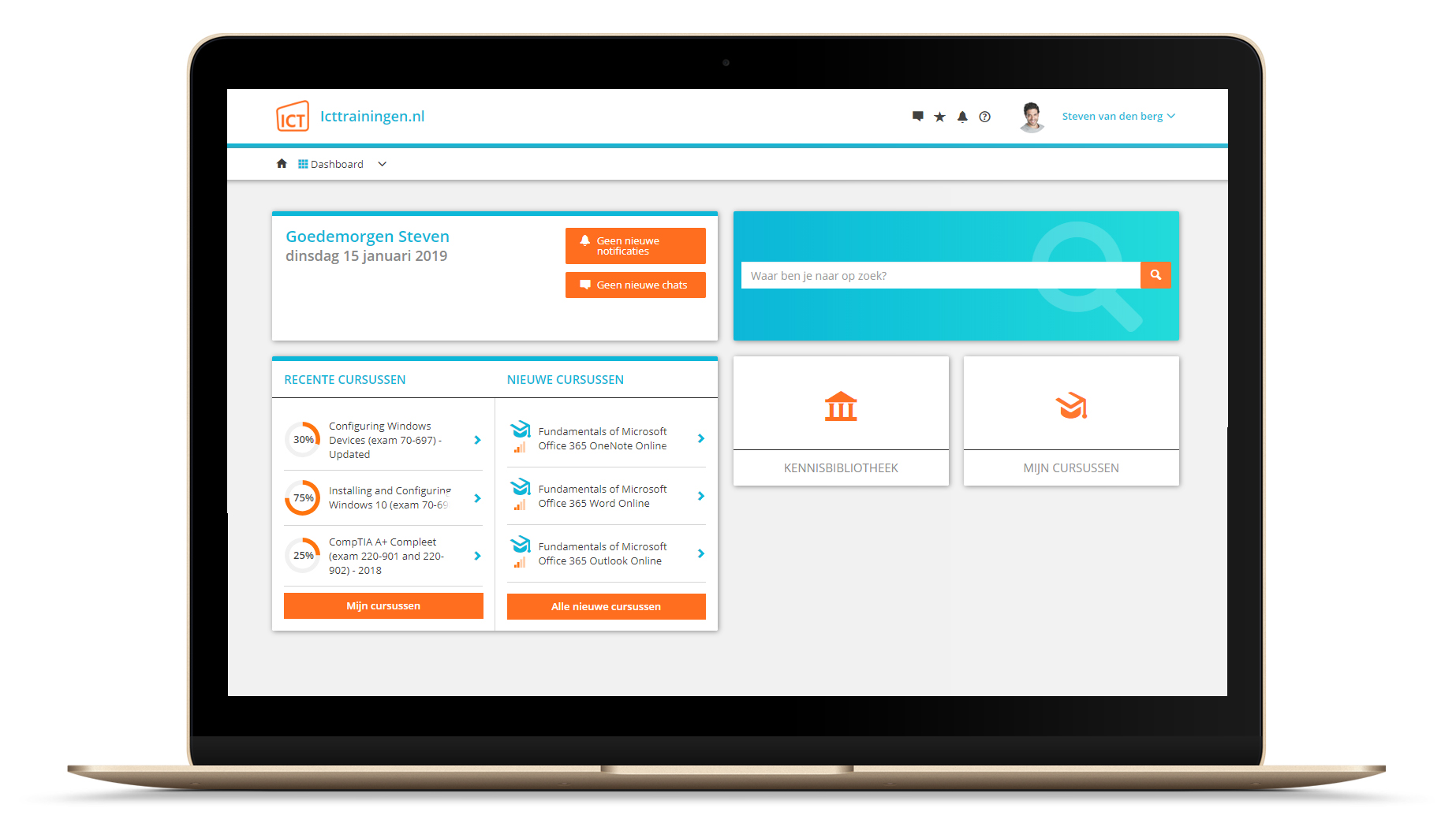
Platform
Na bestelling van je training krijg je toegang tot ons innovatieve leerplatform. Hier vind je al je gekochte (of gevolgde) trainingen, kan je eventueel cursisten aanmaken en krijg je toegang tot uitgebreide voortgangsinformatie.
FAQ
Niet gevonden wat je zocht? Bekijk alle vragen of neem contact op.