Course: CompTIA Security+ (Exam: SY0-601)
As low as
duration: 25 hours |
Language: English (US) |
access duration: 180 days |

Details
CompTIA Security+ is a global certification that validates the
baseline skills necessary to perform core security functions and
pursue an IT security career. Security+ is aligned to the latest
trends and techniques – covering the most core technical skills in
risk assessment and management, incident response, forensics,
enterprise networks, hybrid/cloud operations, and security
controls, ensuring high-performance on the job.
You learn how to assess the security status of an organization. You will learn to recommend the right security solutions and to implement them. Identify, analyze and respond to security events and incidents. You also learn to secure a hybrid environment, such as the cloud.
In this training you will become acquainted with different types of attacks, such as malware attacks, application attacks and network attacks. You learn how to protect the infrastructure against this. You will also discover everything about social engineering techniques, such as phishing, hoaxes and intelligence gathering. And much more.
This training prepares you optimally for the CompTIA Security + (SY0-601) exam.
Result
After successful completion of this training you can:
- Assess the security posture of an enterprise environment and recommend and implement appropriate security solutions
- Monitor and secure hybrid environments, including cloud, mobile, and IoT
- Operate with an awareness of applicable laws and policies, including principles of governance, risk, and compliance
- Identify, analyze, and respond to security events and incident
This training prepares you optimally for the CompTIA Security + (SY0-601) exam.
Prerequisites
We advise CompTIA Network+ and two years of experience in IT administration with a security focus
Target audience
Security Specialist
Content
CompTIA Security+ (Exam: SY0-601)
SYO-601 - CompTIA Security+: Social Engineering Techniques & Attack Types
Common attack types social engineers use target victims using a
- long list of examples such as phishing, smishing, vishing,
- pretexting, pharming, tailgaiting, and shoulder surfing. In this
- course, you'll learn about various social engineering techniques
- including types of phishing, hoaxes, and intelligence gathering.
- Then you'll move on to examine influence campaigns and the reasons
- for social engineering effectiveness. Next, you'll learn about
- malware attacks including password attacks, physical attacks,
- supply-chain, and cryptographic attacks. Finally, you'll explore
- adversarial AI, and cloud-based vs. on-premise attacks. This course
- can be used in preparation for the CompTIA Security+ SYO-601
- certification exam.
SYO-601 - CompTIA Security+: Analyzing Application & Network Attacks
It is crucial that you be able to recognize various application
- and network attacks and be able to protect your infrastructure from
- them. In this course, you'll learn to analyze different application
- attacks such as privilege escalation, cross-site scripting, request
- forgery, injection, code, and APIs. You'll also look at other
- attacks like SSL stripping, pass the hash, and driver manipulation.
- Then, you'll move on to explore a variety of network attacks,
- including wireless, man-in-the-middle, Layer 2, DNS, DDoS, and
- malicious code or script execution. This course can be used in
- preparation for the CompTIA Security+ SYO-601 certification
- exam.
SYO-601 - CompTIA Security+: Threat Actors, Intelligence Sources, & Vulnerabilities
When guarding against threats and vulnerabilities, it is
- important to understand the various sources of threat and how to
- leverage intelligence sources to mitigate them. In this course,
- you'll learn about threat actors and threat vectors, attributes of
- threat actors and agents, threat intelligence sources such as OSINT
- and the dark web, and various research sources. Then, you'll move
- on to examine different types of vulnerabilities, including
- cloud-based and on-premises, zero-day, weak configurations,
- third-party risks, improper patch management, and legacy platforms.
- Finally, you'll examine various impacts such as data loss and data
- breach, as you prepare for the CompTIA Security+ SYO-601
- certification exam.
SYO-601 - CompTIA Security+: Security Assessment & Penetration Testing Techniques
It is important for security professionals to be aware of
- various security assessment and penetration testing techniques and
- methods. In this course, explore key assessment techniques like
- intelligence fusion, threat hunting, threat feeds, advisories and
- bulletins, vulnerability scans, and false positives/false
- negatives. You will also examine the fundamentals of penetration
- testing including black/blue/gray box methodologies, lateral
- movement , privilege escalation, persistence, and pivoting. Other
- topics include passive and active reconnaissance as well as the
- different exercise teams. This course can be used in preparation
- for the CompTIA Security+ SYO-601 certification exam.
SYO-601 - CompTIA Security+: Security Concepts in an Enterprise Environment
As a security specialist, you need to be familiar with and apply
- a range of security concpets related to operating in an enterprise
- environment. In this course, you'll explore enterprise security
- factors like change and configuration management, as well as data
- sovereignty, protection, and loss prevention. You'll learn about
- hardware security modules, geographical considerations, cloud
- access security brokers. You'll move on to examine response and
- recovery controls, SSL/TLS inspection, and site resiliency.
- Finally, you'll learn about deception and disruption techniques
- using honeypots, honeyfiles, honeynets, fake telemetry, and DNS
- sinkholes. This course can be used in preparation for the CompTIA
- Security+ SYO-601 certification exam.
SY0-601 - CompTIA Security+: Implementing Cybersecurity Resilience
In order to protect your enterprise assets, you should be
- familiar with and know how to apply key cybersecurity resiliency
- concepts. In this course, you'll learn about redundancy concepts
- like geographic dispersal, RAID, and NIC teaming. You'll explore
- replication methods like storage area networking and virtual
- machines. You'll move on to examine various backup types, including
- full, incremental, differential, and snapshot. Next, you'll look at
- non-persistence and high availability concepts. Finally, you'll
- learn about the order of restoration and diversity concepts. This
- course can be used in preparation for the CompTIA Security+ SY0-601
- certification exam.
SY0-601 - CompTIA Security+: Virtualization, Cloud Computing, and Cloud Cybersecurity Solutions
In this course, you'll explore the basics of virtualization
- which is the foundation of modern data center cloud computing
- architecture. You will also learn about VM security, cloud
- computing types and models such as IaaS and hydrid clouds. You'll
- learn about managed security service providers (MSSPs),
- containerization fundamentals, serverless computing, and
- Infrastructure as Code. You'll also learn about cloud storage,
- network, and compute security solutions. This course can be used in
- preparation for the CompTIA Security+ SY0-601 certification
- exam.
SY0-601 - CompTIA Security+: Controls & Application Development, Deployment, & Automation
This CompTIA Security+ course covers some of the most important
- topics in the entire training series. First, the learner will
- discover the NIST control categories used by CompTIA along with the
- five critical control types. The remainder of this course deals
- with vital security concepts related to application development,
- deployment, and automation. Other core topics include various
- DevOps environments, secure coding techniques, OWASP, software
- diversity and automation. This course can be used in preparation
- for the CompTIA Security+ SY0-601 certification exam.
SY0-601 - CompTIA Security+: Authentication & Authorization Design Concepts
Authentication and authorization are very closely related but
- have specific roles to play in security. In this CompTIA Security+
- SY0-601 course you will explore authentication, authorization, and
- accounting (AAA) services, directory services, federation and
- attestation, smart-card and biometrics, and multi-factor
- authentication. This course can be used in preparation for the
- CompTIA Security+ SY0-601 certification exam.
SY0-601 - CompTIA Security+: Implementing Identity and Account Management & AAA Solutions
Identity and access management (IAM) is used to protect your
- data by ensuring the right users have access to the right
- resources. This CompTIA Security+ SY0-601 course covers various
- identity controls including identity providers, attributes,
- certifications, tokens, and SSH keys. It also discusses the use of
- different account types and common account policies, and
- authentication management techniques such as password keys,
- password vaults, TPM, HSM, and knowledge-based authentication.
- Finally, you learn about protocols and services used for federation
- and single sign-on, and access control schemes like ABAC, DAC,
- RBAC, and MAC. This course can be used in preparation for the
- CompTIA Security+ SY0-601 certification exam.
SY0-601 - CompTIA Security+: Physical Security Controls
In this CompTIA Security+ SY0-601 course you will realize that
- real security begins with physical security. You will explore a
- wide array of physical security controls including bollards,
- barricades, and badges. You will discover the importance of
- controls like alarms, signage, cameras, motion recognition and
- detection. You will answer many questions about the security guards
- as well. Other important topics include locks, biometrics,
- lighting, fencing, fire suppression, sensors, motion detection,
- faraday cages, air gapping, and secure data destruction techniques.
- This course can be used in preparation for the CompTIA Security+
- SY0-601 certification exam.
SYO-601 - CompTIA Security+: Security Policies, Regulations, Standards, & Frameworks
Whether you're an employee or contractor, this CompTIA Security+
- SYO-601 course will have something you can use to improve the
- organizational security at your workplace. You'll start by
- examining security topics related to the hiring to release process,
- such as background checks and investigations, non-disclosure
- agreements, acceptable use policy, and onboarding and offboarding.
- You'll move on to explore further personnel policies, including job
- rotation, mandatory vacations, separation of duties, clean desk
- space, and social media usage. You'll then recognize some useful
- security awareness practices, such as phishing simulations,
- computer-based training, role-based training, and diversity
- training techniques. Finally, you'll identify various business
- agreements, account types, regulations, and governance, such as
- GDPR, PCI DSS, CIS, NIST, and ISO. This course is part of a series
- that prepares the learner for the CompTIA Security+ (SY0-601)
- exam.
SY0-601 - CompTIA Security+: Basic Cryptography & Public Key Infrastructure
To prepare for the CompTIA Security+ SY0-601 certification exam,
- you will need to be able to identify and describe basic
- cryptography concepts and their application in everyday use. You'll
- also need to recognize common aspects of Public Key Infrastructure
- (PKI). In this CompTIA Security+ SY0-601 course, you'll compare
- symmetric and asymmetric cryptography, recognize the
- characteristics of a cryptographic key, and contrast block and
- stream cipher operations. You'll explore the purpose and features
- of cryptographic hashing, common key exchange mechanisms, and
- various next-generation concepts such as lightweight cryptography,
- quantum and post-quantum computing, and homomorphic encryption.
- You'll move on to identify the main aspects and core concepts
- associated with Public Key Infrastructure (PKI). Finally, you'll
- distinguish several types of certificates and review different
- certificate formats.
SY0-601 - CompTIA Security+: Implementing Secure Protocols & Application Security Solutions
In this CompTIA Security+ SYO-601 course, you'll explore a variety of core secure protocols.
You'll examine Domain Name System Security Extension (DNSSEC), SSH, Secure/Multipurpose Internet Mail Exchanger (S/MIME), Secure Real-time Protocol (SRTP), LDAPS, File Transfer Protocol Secure (FTPS), Secured File Transfer Protocol (SFTP), Simple Network Management Protocol version 3 (SNMPv3), Hypertext Transfer Protocol over SSL/TLS (HTTPS), IPsec, Authentication Header (AH), and Encapsulated Security Payload (ESP) and its tunnel/transport modes.
You'll move on to list several use cases for these concepts. You'll then describe endpoint protection, boot integrity mechanisms, database security mechanisms, and hardening targets. Finally, you'll identify several advanced application security techniques. This course can be used in preparation for the CompTIA Security+ SYO-601 certification exam.
SYO-601 - CompTIA Security+: Implementing Secure Network Designs
Networking has always been one of the primary paths to becoming a security expert. This CompTIA Security+ SYO-601 course involves recognizing how to implement secure networking environments and designs.
In this course, you'll explore the concepts, techniques, and deployments involved in the following valuable network security technologies: load balancing, networking segmentation/zoning, and virtual private networks. Next, you'll examine several switch port security techniques, such as BPDU guard, DHCP snooping, and MAC filtering. You'll then recognize the various features of firewalls, such as ACLs and WAF, and compare network appliance solutions, such as port spanning, NAC, NIDS, and NIPS.
Finally, you'll outline advanced network environment solutions, like route security, IPv6, and next-gen monitoring. This course can be used in preparation for the CompTIA Security+ SYO-601 certification exam.
SYO-601 - CompTIA Security+: Wireless, Mobile, & Embedded Device Security
"This domain encompasses one of the most rapidly changing and evolving sets of technologies. It also represents one of the most significant changes from the previous Security+ exam. In this CompTIA Security+ SYO-601 course, you'll explore a broad range of communication solutions based on the fundamental aspects of wireless, mobile, and embedded system technology security.
You'll learn about a variety of specialized systems and concepts, including wireless cryptographic and authentication protocols, wireless security methods and installation, mobile connection methods and receivers, device types and deployment models, MDM and MAM, mobility enforcement and monitoring, and various embedded and specialized systems.
By gaining knowledge in these areas, you will be prepared for a career in the world's most cutting-edge industries. This course can be used in preparation for the CompTIA Security+ SYO-601 certification exam."
SYO-601 - CompTIA Security+: Organizational Security Assessment tools & Mitigation Controls
To prepare for the CompTIA Security+ SYO-601 certification exam, you will need to identify and describe popular organizational security assessment tools and risk mitigation controls. You will likely come across these tools at some point in your career, so prior knowledge of how these work and what they're used for will be highly beneficial.
In this CompTIA Security+ SYO-601 course, you'll explore the concept of network reconnaissance and discovery, and examine packet capture and replay, file manipulation, and forensic tools. You'll also identify shell and script environments, exploitation kits, and password crackers. You'll move on to recognize methods for reconfiguring endpoint security solutions and describe configuration changes for mitigation, the concepts of isolation, containment, and segmentation, and secure orchestration, automation, and response (SOAR) solutions. This course can be used in preparation for the CompTIA Security+ SYO-601 certification exam.
SYO-601 - CompTIA Security+: Incident Response, Digital Forensics, & Supporting Investigations
To best support a digital forensic investigation, incident response teams need to be aware of the various incident response plans and processes available to them. In this CompTIA Security+ SYO-601 course, you'll start by exploring various incident response exercises, such as tabletop sessions, walkthroughs, and simulations. Then, you'll outline three fundamental attack frameworks: MITRE, The Diamond Model of Intrusion Analysis, and the Cyber Kill Chain.
Next, you'll examine different incident response plans types, including communication plans, disaster recovery plans, business continuity plans, and continuity of operation planning (COOP). You'll then identify key aspects of digital forensics, such as documentation/evidence, acquisition and integrity maintenance, preservation, e-discovery, data recovery, non-repudiation, and strategic intelligence and counterintelligence. Lastly, you'll outline how to utilize appropriate digital forensic data sources to support an investigation.
SYO-601 - CompTIA Security+: Risk Management, Privacy, & Sensitive Data Security
In this CompTIA Security+ SYO-601 course, you'll explore some advanced security concepts and build on some you may already know. The main topics you'll examine are risk management, privacy issues, and sensitive data management.
You'll start by recognizing the essential aspects and considerations of risk types, risk management strategies, risk analysis, and disasters. You'll then review the business impact analysis (BIA) aspect of business continuity planning. Moving on to sensitive data security, you'll identify privacy breach consequences, data classification types, and associated roles and responsibilities.
You'll also outline privacy protection measures, such as notifications of privacy breaches, privacy-enhancing technologies, and advanced privacy concepts, like impact assessments and privacy notices. This course is part of a series that prepares you for the CompTIA Security+ (SY0-601) exam.
SYO-601 - CompTIA Security+: Monitoring, Visibility, & Reporting
In this CompTIA Security+ SYO-601 course, you'll bring your
- existing security knowledge together to prepare the delivery of
- your work's output and results to executive management, C-suite,
- and other stakeholders. You'll start by exploring how to take
- advantage of Windows and Linux logging and monitoring. You'll then
- examine how to work with protocol analyzer output, cloud computing
- tools, and log aggregation and collection. Next, you'll identify
- some best practices and guidelines to use when working with
- visibility and reporting. Finally, you'll outline how to identify
- lessons learned and create after-action reports. This course is
- part of a series that prepares you for the CompTIA Security+
- (SY0-601) exam.
Course options
We offer several optional training products to enhance your learning experience. If you are planning to use our training course in preperation for an official exam then whe highly recommend using these optional training products to ensure an optimal learning experience. Sometimes there is only a practice exam or/and practice lab available.
Optional practice exam (trial exam)
To supplement this training course you may add a special practice exam. This practice exam comprises a number of trial exams which are very similar to the real exam, both in terms of form and content. This is the ultimate way to test whether you are ready for the exam.
Optional practice lab
To supplement this training course you may add a special practice lab. You perform the tasks on real hardware and/or software applicable to your Lab. The labs are fully hosted in our cloud. The only thing you need to use our practice labs is a web browser. In the LiveLab environment you will find exercises which you can start immediately. The lab enviromentconsist of complete networks containing for example, clients, servers,etc. This is the ultimate way to gain extensive hands-on experience.
Sign In
WHY_ICTTRAININGEN
Via ons opleidingsconcept bespaar je tot 80% op trainingen
Start met leren wanneer je wilt. Je bepaalt zelf het gewenste tempo
Spar met medecursisten en profileer je als autoriteit in je vakgebied.
Ontvang na succesvolle afronding van je cursus het officiële certificaat van deelname van Icttrainingen.nl
Krijg inzicht in uitgebreide voortgangsinformatie van jezelf of je medewerkers
Kennis opdoen met interactieve e-learning en uitgebreide praktijkopdrachten door gecertificeerde docenten
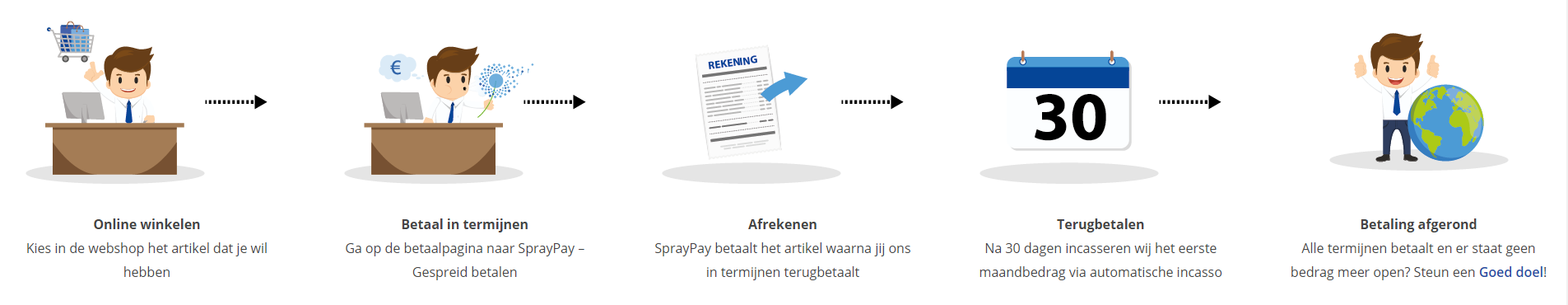
Orderproces
Once we have processed your order and payment, we will give you access to your courses. If you still have any questions about our ordering process, please refer to the button below.
read more about the order process
Een zakelijk account aanmaken
Wanneer u besteld namens uw bedrijf doet u er goed aan om aan zakelijk account bij ons aan te maken. Tijdens het registratieproces kunt u hiervoor kiezen. U heeft vervolgens de mogelijkheden om de bedrijfsgegevens in te voeren, een referentie en een afwijkend factuuradres toe te voegen.
Betaalmogelijkheden
U heeft bij ons diverse betaalmogelijkheden. Bij alle betaalopties ontvangt u sowieso een factuur na de bestelling. Gaat uw werkgever betalen, dan kiest u voor betaling per factuur.

Cursisten aanmaken
Als u een zakelijk account heeft aangemaakt dan heeft u de optie om cursisten/medewerkers aan te maken onder uw account. Als u dus meerdere trainingen koopt, kunt u cursisten aanmaken en deze vervolgens uitdelen aan uw collega’s. De cursisten krijgen een e-mail met inloggegevens wanneer zij worden aangemaakt en wanneer zij een training hebben gekregen.
Voortgangsinformatie
Met een zakelijk account bent u automatisch beheerder van uw organisatie en kunt u naast cursisten ook managers aanmaken. Beheerders en managers kunnen tevens voortgang inzien van alle cursisten binnen uw organisatie.
What is included?
| Certificate of participation | Yes |
| Monitor Progress | Yes |
| Award Winning E-learning | Yes |
| Mobile ready | Yes |
| Sharing knowledge | Unlimited access to our IT professionals community |
| Study advice | Our consultants are here for you to advice about your study career and options |
| Study materials | Certified teachers with in depth knowledge about the subject. |
| Service | World's best service |
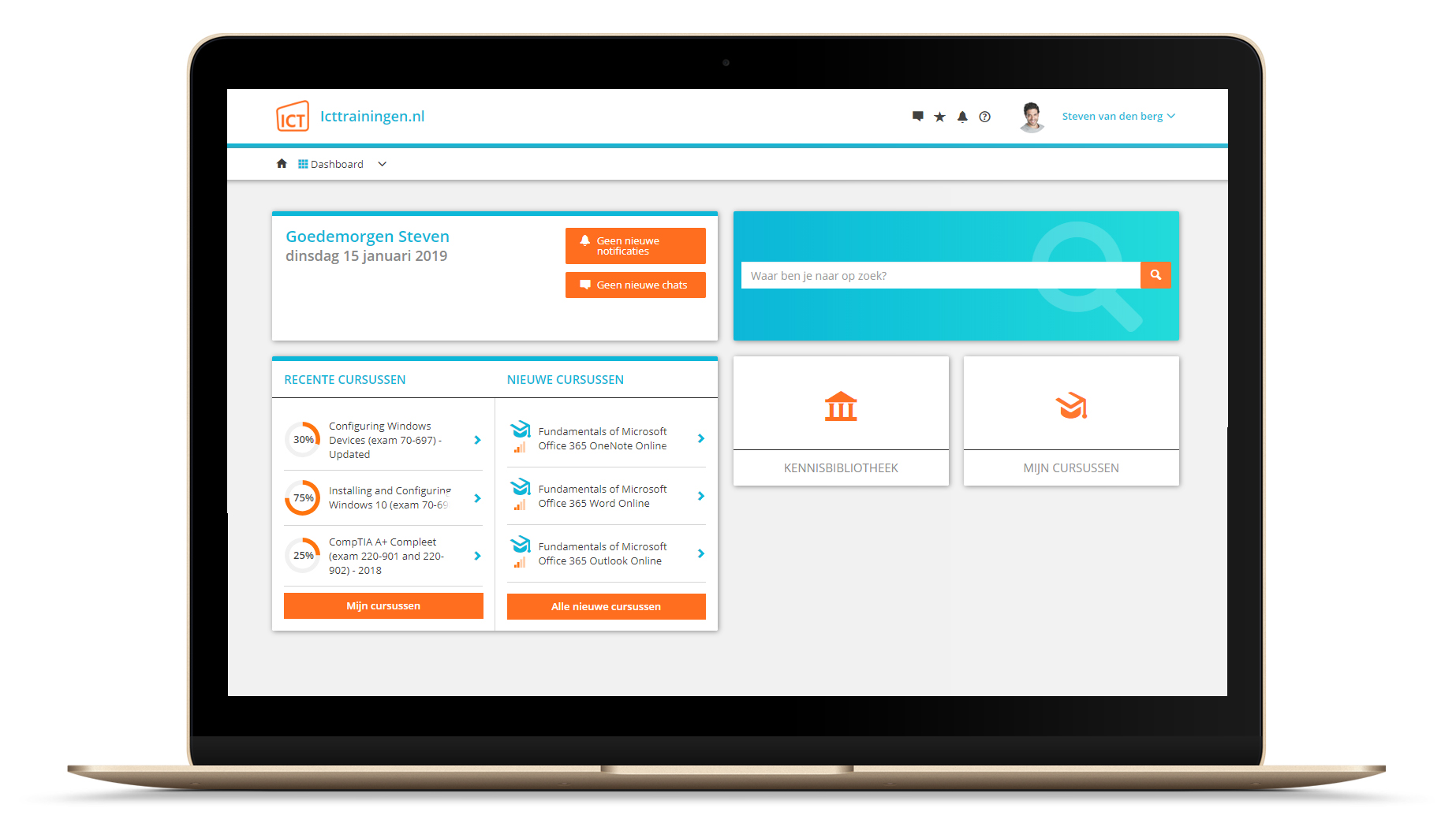
Platform
Na bestelling van je training krijg je toegang tot ons innovatieve leerplatform. Hier vind je al je gekochte (of gevolgde) trainingen, kan je eventueel cursisten aanmaken en krijg je toegang tot uitgebreide voortgangsinformatie.
FAQ
Niet gevonden wat je zocht? Bekijk alle vragen of neem contact op.