Course: Certified Information Systems Auditor (CISA)
duration: 38 hours |
Language: English (US) |
access duration: 180 days |

Details
The Certified Information Systems Auditor (CISA) is a globally recognised certification that validates professionals in IT auditing, control and security. Earning the CISA certification is proof of knowledge and skills in IT governance, risk management and information security.
The following areas of certification are covered in this course:
- The Process of Auditing Information Systems
- Governance and Management of IT
- Information Systems Acquisition, Development and Implementation
- Information Systems Operations, Maintenance and Support
- Protection of Information Assets
Result
After completing this course, you'll possess a comprehensive understanding of key audit principles, IT management frameworks, and security measures necessary for ensuring the integrity, confidentiality, and availability of information assets within an organization's technological landscape.
Prerequisites
You have general knowledge of IT concepts. To obtain the CISA certificate you must prove that you have practical experience.
Target audience
Security Specialist
Content
Certified Information Systems Auditor (CISA)
CISA 2022: Information Systems Auditing
Successful organizations implement information systems (IS) auditing, controls, monitoring, and assessments of their IT and business systems. In this course, you will discover the keys to conducting a successful audit. First, you will be introduced to information systems auditing, beginning with an explanation of why we audit. Then you will examine the Information Systems Audit and Control Association (ISACA) code of professional ethics and review IS auditing procedures and ISACA auditing standards. Next, you will explore business procedures and controls, risk-based auditing, and other types of audits. Finally, you will investigate auditing project management, audit planning, audit scheduling, urgent incident discovery, and audit reporting. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Auditing, Data Analysis, & Controls
Successful information systems (IS) auditing requires many components and controls, beginning with the nature of a business, its driving processes, and underlying IT solutions. In this course, you will discover auditing, data analysis, and control, beginning with audit findings remediation follow-up, sampling methods, and audit evidence gathering. Then you will explore data analytics and systems auditing, the role of the data analyst, and auditing quality assurance. Next, you will focus on organizational documentation and stakeholder needs. Finally, you will learn about network diagrams, types of security controls, and control objectives and controls. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: IT Management Frameworks, Regulations, & Standards
IT management frameworks provide a structured approach to managing and auditing IT assets. Regulations and standards are put in place to ensure that organizations have guidelines to follow for how they deal with information systems. In this course, you will explore IT management frameworks, regulations, and standards, beginning with an overview of IT and data governance, and standards, policies, and procedures. Then you will learn about Control Objectives for Information and Related Technologies (COBIT), IT Infrastructure Library (ITIL), and International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC) standards. Next, you will discover risk management and risk treatment. Finally, you will dig into IT maturity models, the Business Model for Information Security (BMIS), the Information Technology Assurance Framework (ITAF), and IT balanced scorecards. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: IT Resources & Monitoring
CISA 2022: Technology resources, service level management, monitoring, and quality management all play crucial roles in information systems management and represent key areas of focus for information system (IS) auditing. In this course, you will explore IT resources and monitoring, beginning with a review of common technology components, IT resource management, service-level management, and service-level agreements. Then you will learn about performance baselines, Windows and Linux performance monitoring, and cloud-based performance monitoring and alerts. Finally, you will discover key aspects of quality management, IT quality management frameworks, and quality management best practices. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Projects, Development, & Testing
Project governance, management, system development, and testing play key roles in information systems. In this course, you will begin by exploring project governance and management, project governance best practices, business cases, and feasibility studies. Then, you will dig into system development methodologies and control identification and design. Finally, you will learn about testing methodologies, beginning with an overview of software testing, unit testing, regression testing, acceptance testing, integration testing, performance testing, and fuzzing. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Information Systems Management
Effective IT management provides a structured approach to managing and auditing IT assets. It also provides a foundation for auditing, an important feature for information system (IS) auditors. In this course, you will discover key facets of information systems management, beginning with system interfaces and end-user computing. Then you will examine change management, configuration management, and vulnerability management. Finally, you will explore group policy configuration delegation, Microsoft Configuration Manager configuration management, Microsoft Configuration Manager patch deployment, and job scheduling. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Information Systems Development & Implementation
Systems planning, testing, integration, and delivery are key elements of ensuring the timely delivery of system changes or entirely novel solutions. In this course, you will explore the phases of the system development life cycle (SDLC) and IT project management. Next, you will examine continuous integration and delivery (CI/CD) and process improvement, including advantages and common methodologies. Then you will discover infrastructure deployment, system migration and data conversion, and cloud migration assessments. Finally, you will learn about the post-implementation review process and post-implementation activities and best practices. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Data Privacy
Any IT environment requires a firm understanding of data privacy. Privacy laws and regulations, combined with industry practices, form the basis for effective information protection. In this course, you'll explore data privacy, beginning with the CIA Triad, personally identifiable information (PII), and Protected Health Information (PHI). You will learn about the General Data Protection Regulation (GDPR), Payment Card Industry Data Security Standard (PCI DSS), compliance with GDPR and PCI DSS, the Health Insurance Portability and Accountability Act (HIPAA), and Federal Risk and Authorization Management Program (FedRAMP). Finally, you'll dig into assets and risks, annualized loss expectancy (ALE), and network inventories. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: IAM & Data Classification
Identity and access management (IAM) and data classification play key roles in the protection of access via authentication and authorization. In this course, you'll explore IAM and data classification principles, beginning with authentication and authorization, on-premises IAM, cloud-based IAM, and multi-factor authentication (MFA). Then you'll learn about Azure MFA, Azure Role-based Access Control (RBAC), Amazon Web Services (AWS) RBAC, and Microsoft Entra ID delegated administration. Finally, you'll dig into identify federation, data tagging, file system permissions, File Server Resource Manager (FSRM), and Dynamic Access Control. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Securing Networks & IT Assets
In any enterprise information technology environment, network and IT assets must be secured in order to preserve the integrity and legal standing of the organization. In this course, you will discover key aspects of securing networks and IT assets, beginning with network attacks, network threat mitigation, firewalls, and security monitoring and testing. Then you will explore the identification of plaintext network traffic, implementation of a packet filtering firewall, and implementation of a content filtering firewall. Finally, you will learn about physical asset protection, focusing on heating, ventilation, and air conditioning (HVAC) systems, physical security, drones and proximity security, and fire suppression systems. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Protecting Information Assets
Information is a primary asset of most organizations today. It has a real value and, if compromised, could have real implications for the enterprise. In this course, you will explore considerations for protecting information assets, beginning with cryptography, asymmetric and symmetric encryption, Windows Encrypting File System, and Windows BitLocker. Then, you will learn about file integrity, the public key infrastructure (PKI) hierarchy, the PKI certificate life cycle, and private certificate authorities (CAs). Finally, you will discover certificate templates, manual certificate issuance, securing network traffic, disabling SSLv3, enabling an HTTPS website, and client Secure Sockets Layer (SSL)/Transport Layer Security (TLS) certificates. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Protecting Digital Assets
Digital asset protection is a key concern for the modern enterprise. As most organizations rely heavily on information systems in their day-to-day operations, protecting these valuable assets is of paramount importance. In this course, you'll learn about digital asset protection principles, beginning with organizational security policies, security and the OSI model, password security, and endpoint security. Then, you'll explore data loss prevention (DLP), Internet of Things (IoT) devices, IoT device vulnerability, and IoT security. Finally, you'll dig into mobile device access control, mobile device hardening, mobile device policies, and malicious app store apps. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Virtualization & Cloud Computing
Virtualization is such an important technology today that it is rather surprising that a little more than a decade ago, it was not given much consideration as a practical way of providing cloud-based services. Today, it is difficult to imagine life without virtualization. In this course, you will explore virtualization and cloud computing, beginning with an overview of virtualization technologies, hypervisors, and virtual network switches. Then you will dig into creating a virtual machine and hardening a virtualized environment. Next, you will investigate cloud computing, common cloud service offerings, and cloud security. Finally, you will learn about Windows cloud-based virtual machines, Linux cloud-based virtual machines, and cloud endpoint security. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Data Storage & Malware
Data storage and malware get their fair share of attention when considering data, information, and privacy. Rightly so, as they represent key concerns for the security-minded information technology manager. In this course, explore data storage and malware, beginning with an overview of data vs. information, big data and data analytics, and storage area network (SAN) security. Next, learn how to secure an iSCSI SAN and about cloud storage security, storage media disposal, database security, and database availability. Finally, examine data backup and restore strategies, cloud-based data backups, social engineering, and security awareness training. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Business Continuity
Downtime has disastrous results, beginning with lost revenues but hardly ending there. Reputation, trust, and confidence all rely on enterprises being able to continue operating in the event of a disaster, natural or otherwise. In this course, you'll explore aspects of business continuity, beginning with high availability, business continuity, and business impact analysis (BIA), disaster recovery plans (DRPs), and business continuity plans (BCPs). Then you'll dig into incident response plans (IRPs), alternate recovery sites, and Redundant Arrays of Independent Disks (RAID). Finally, you'll learn about RAID configuration and data replication across regions. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: System Development & Vulnerability Testing
Systems development and vulnerability testing often go hand in hand to ensure the timely delivery of system changes or entire new solutions. In this course, you'll learn about system development and vulnerability testing, beginning with secure coding, security testing types, vulnerability scanning, and how to perform a vulnerability scan. Then you'll explore comparing network scans, penetration testing, packet forgery, and web application vulnerability scans. Finally, you'll dig into IPsec network traffic, jump boxes, and honeypots. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Digital Evidence Gathering
When conducting an audit, the collection of evidence is imperative in order to properly and completely evaluate an information system. Appropriate care must be taken when gathering, handling, and storing digital evidence so that it remains admissible in a court of law. In this course, you'll explore the principles of digital evidence gathering, beginning with digital forensics, digital forensics hardware, and digital forensics software. Then, you'll dig into order of volatility, chain of custody, and forensic data browsing. Finally, you'll learn about forensic file recovery and hard disk imaging. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Continuous Monitoring
Enterprise systems have continuous monitoring needs, of both business processes and supporting IT solutions. Information systems (IS) auditing can identify where improvements can be made. In this course, you will explore continuous monitoring, beginning with an overview of continuous monitoring, business processes, and sampling types. Then you will discover how to filter Windows logs and forward Linux logs. Next, you will focus on packet capturing placement and analysis. Finally, you will dig into security information and event management (SIEM), intrusion detection systems (IDSs), and intrusion prevention systems (IPSs). This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
CISA 2022: Auditing Scenarios
IT technicians and managers are responsible for the safety of IT processing systems and sensitive data. Information system audit processes, if applied effectively, can ensure adequate risk mitigation. In this course, you will explore auditing scenarios, beginning with IT key performance indicators (KPIs), audit planning, and security control cost-effectiveness. Then, you'll learn how to determine Wi-Fi weakness and secure traveling users. Finally, you'll dig into key usage and compensating control selection. This course helps prepare learners for the ISACA certification exam, Certified Information Systems Auditor (CISA).
Course options
We offer several optional training products to enhance your learning experience. If you are planning to use our training course in preperation for an official exam then whe highly recommend using these optional training products to ensure an optimal learning experience. Sometimes there is only a practice exam or/and practice lab available.
Optional practice exam (trial exam)
To supplement this training course you may add a special practice exam. This practice exam comprises a number of trial exams which are very similar to the real exam, both in terms of form and content. This is the ultimate way to test whether you are ready for the exam.
Optional practice lab
To supplement this training course you may add a special practice lab. You perform the tasks on real hardware and/or software applicable to your Lab. The labs are fully hosted in our cloud. The only thing you need to use our practice labs is a web browser. In the LiveLab environment you will find exercises which you can start immediately. The lab enviromentconsist of complete networks containing for example, clients, servers,etc. This is the ultimate way to gain extensive hands-on experience.
Sign In
WHY_ICTTRAININGEN
Via ons opleidingsconcept bespaar je tot 80% op trainingen
Start met leren wanneer je wilt. Je bepaalt zelf het gewenste tempo
Spar met medecursisten en profileer je als autoriteit in je vakgebied.
Ontvang na succesvolle afronding van je cursus het officiële certificaat van deelname van Icttrainingen.nl
Krijg inzicht in uitgebreide voortgangsinformatie van jezelf of je medewerkers
Kennis opdoen met interactieve e-learning en uitgebreide praktijkopdrachten door gecertificeerde docenten
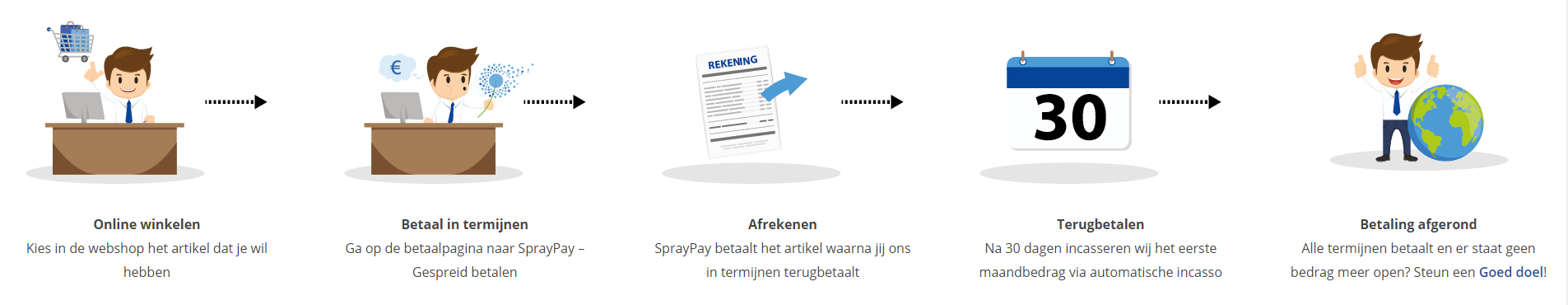
Orderproces
Once we have processed your order and payment, we will give you access to your courses. If you still have any questions about our ordering process, please refer to the button below.
read more about the order process
Een zakelijk account aanmaken
Wanneer u besteld namens uw bedrijf doet u er goed aan om aan zakelijk account bij ons aan te maken. Tijdens het registratieproces kunt u hiervoor kiezen. U heeft vervolgens de mogelijkheden om de bedrijfsgegevens in te voeren, een referentie en een afwijkend factuuradres toe te voegen.
Betaalmogelijkheden
U heeft bij ons diverse betaalmogelijkheden. Bij alle betaalopties ontvangt u sowieso een factuur na de bestelling. Gaat uw werkgever betalen, dan kiest u voor betaling per factuur.

Cursisten aanmaken
Als u een zakelijk account heeft aangemaakt dan heeft u de optie om cursisten/medewerkers aan te maken onder uw account. Als u dus meerdere trainingen koopt, kunt u cursisten aanmaken en deze vervolgens uitdelen aan uw collega’s. De cursisten krijgen een e-mail met inloggegevens wanneer zij worden aangemaakt en wanneer zij een training hebben gekregen.
Voortgangsinformatie
Met een zakelijk account bent u automatisch beheerder van uw organisatie en kunt u naast cursisten ook managers aanmaken. Beheerders en managers kunnen tevens voortgang inzien van alle cursisten binnen uw organisatie.
What is included?
| Certificate of participation | Yes |
| Monitor Progress | Yes |
| Award Winning E-learning | Yes |
| Mobile ready | Yes |
| Sharing knowledge | Unlimited access to our IT professionals community |
| Study advice | Our consultants are here for you to advice about your study career and options |
| Study materials | Certified teachers with in depth knowledge about the subject. |
| Service | World's best service |
Platform
Na bestelling van je training krijg je toegang tot ons innovatieve leerplatform. Hier vind je al je gekochte (of gevolgde) trainingen, kan je eventueel cursisten aanmaken en krijg je toegang tot uitgebreide voortgangsinformatie.
FAQ
Niet gevonden wat je zocht? Bekijk alle vragen of neem contact op.