Course: Implementing and Operating Cisco Security Core Technologies (CCNP security-SCOR Exam: 350-701)
duration: 26 hours |
Language: English (US) |
access duration: 180 days |

Details
In this training, Implementing and Operating Cisco Security Core Technologies (SCOR), you will learn skills and technologies that you need to implement key Cisco security solutions. With the aim of providing advanced protection against cyber attacks. In this training you will be introduced to network vulnerabilities. You will also research various security techniques that you can use to protect the network against security attacks.
In this training you will learn about:
- Securing networks.
- Cloud and content.
- Endpoint protection.
- Secure network access.
- Visibility and enforcement.
In addition, you will gain extensive hands-on experience with implementing Cisco Firepower® Next-Generation Firewall and Cisco Adaptive Security Appliance (ASA) Firewall; configure access control policies, email policies and more. You will also get an introduction to Cisco Stealthwatch® Enterprise and Cisco Stealtwatch Cloud Threat Detection Features.
Finally, this training prepares you optimally for the Cisco CCNP Security certification. To obtain the CCNP security certificate, you must pass two exams: the Core exam and one of the concentration exams. The Core exam focuses on your knowledge of security infrastructure. The concentration exams focus on emerging and industry-specific topics. This training prepares you for the CCNP Security Core exam and the CCIE Security Core exam. By passing the Core exam, you are eligible to schedule and take the CCIE lab within the validity period of your Core exam.
Result
When you have successfully completed this training, you will be familiar with various security techniques that you can use to protect the network against security attacks. In addition, you are optimally prepared for the CCNP Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) exam.
Prerequisites
Attendees should meet the following prerequisites:
- Familiarity with Ethernet and TCP/IP networking
- Working Knowledge of the Windows operating system
- Working Knowledge of Cisco IOS networking and concepts
- Familiarity with basics of networking security concepts
Target audience
System Administrator, Network Administrator, Security Specialist
Content
Implementing and Operating Cisco Security Core Technologies (CCNP security-SCOR Exam: 350-701)
SCOR: Security Basics & Common Threats
In this course, you'll first review basic SCOR concepts and why
- they are important. Next, you'll move on to explore common language
- when it comes to securing your lT architecture and how to correctly
- use this language when discussing your security environment. You'll
- examine common attack methods in order to properly secure your
- on-prem IT environment. With the popularity of the cloud, computer
- criminals have begun targeting these areas with more and more
- frequency. To wrap up this course, you'll learn about some of the
- most common attacks against the cloud. This course can be used in
- preparation for the 350-701: Implementing and Operating Cisco
- Security Core Technologies (SCOR) certification exam.
SCOR: Security Vulnerabilities, Attack Mitigations, & Cryptographic Solutions
There are many common vulnerabilities in software and systems
- and you must understand them to effectively secure your network
- systems. In this course, you'll learn about some of these
- vulnerabilities, as well as common attack mitigation techniques for
- network application style attacks. Before reviewing cybersecurity
- technologies in greater detail, you'll first look at the basics of
- cryptography and the critical role it plays in computer and network
- security. Finally, you'll explore some current cryptographic
- solutions and what they are used for. This course can be used in
- preparation for the 350-701: Implementing and Operating Cisco
- Security Core Technologies (SCOR) certification exam.
SCOR: PKI & IKE
A major aspect of Internet-based security these days hinges upon
- the Public Key Infrastructure. In this course, you'll learn the
- basics of this critical set of technologies. PKI is the magic
- behind the use of seamless SSL/TLS authentication and encryption on
- the public Internet and this clever implementation of asymmetric
- encryption algorithms can also be used in your private enterprise.
- You'll continue your exploration of PKI by learning how to fulfill
- a certificate request. Finally, you'll learn about the Internet Key
- Exchange, including the differences between IKE v1 and v2. This
- course can be used in preparation for the 350-701: Implementing and
- Operating Cisco Security Core Technologies (SCOR) certification
- exam.
SCOR: VPNs, Security Intelligence, & Social Engineering Attacks
There is no denying it, VPN is a hugely popular part of the
- modern Internet. In this course, you'll learn about different types
- of VPN, its uses, and various technologies you can use. Next,
- you'll explore security devices and their ability to help you
- author, share, and consume security intelligence data. You'll
- examine social engineering attacks that are very prevalent today,
- including how to protect against them and the software you can use
- for defense. Finally, you'll learn about some of the most common
- attacks today, including many different variations of phishing
- attacks. This course can be used in preparation for the 350-701:
- Implementing and Operating Cisco Security Core Technologies (SCOR)
- certification exam.
SCOR: SDN APIs & Security Appliance API Calls
In this course, you'll learn about SDN and the northbound and
- southbound APIs used with it. You'll also learn about the RESTful
- APIs that you can make use of for the programmability of your Cisco
- security devices. You'll also discover how these API calls can be
- used in an actual network environment and how to quickly get
- started with programmatic code referencing these important APIs.
- This course can be used in preparation for the 350-701:
- Implementing and Operating Cisco Security Core Technologies (SCOR)
- certification exam.
SCOR: Security Models & Frameworks
There is often confusion about why there are intrusion
- prevention devices when we already have firewalls. Aren't these
- devices doing the same thing? In this course, you'll learn the
- differences between these network security functions and tools.
- You'll also look at some specialized devices in more detail,
- including the Web Security Appliance and the Email Security
- Appliance. You'll move on to explore how you can deploy the ASA and
- Firepower in different ways like routed or transparent mode. Next,
- you'll learn about NetFlow and Flexible NetFlow, valuable tools for
- monitoring the flows of data through your network. You'll also see
- how you can safely leverage the power of Flexible NetFlow to help
- control your network. Finally, you'll learn about techniques for
- adding segmentation to your network, including EPGs in Cisco ACI
- and SGTs. This course can be used in preparation for the 350-701:
- Implementing and Operating Cisco Security Core Technologies (SCOR)
- certification exam.
SCOR: DHCP Snooping, DAI, IP Source Guard, Private VLANs, & Storm Control
When you think about attacking a network with a rogue DHCP
- device, you realize it is such a relatively easy attack to carry
- out. In this course, you'll learn about the DHCP snooping feature
- and how it is configured. Next, you'll examine how multiple
- different security features can leverage the DHCP snooping database
- that results from a proper implementation of DHCP snooping,
- including a demonstration of both the DAI and IP Source Guard
- features. You'll learn about the often intimidating security
- feature private VLANs, including the details of these structures
- and the reason why they exist. Finally, you'll explore traffic
- storms, including when they occur, how they create excessive
- traffic and can degrade network performance, and how to use the
- traffic storm control feature. This course can be used in
- preparation for the 350-701: Implementing and Operating Cisco
- Security Core Technologies (SCOR) certification exam.
SCOR: Port Security, VLAN Hopping, Network Hardening, & Access Control
Port security is not one of the most important features when it
- comes to securing your network and it does have its challenges, but
- this feature is definitely a nice layer of defense in your overall
- defense-in-depth strategy. In this course, you'll learn about port
- security, as well as the VLAN hopping attack and how it can be
- prevented. You'll explore several security techniques you can use
- to help harden the network against security attacks and how it can
- benefit you to break the network and network device functionality
- down into the three planes of operation - management, data, and
- control planes. You'll also examine examples of security
- technologies you can use at each plane of operation to harden the
- overall network. Finally, you'll learn about different approaches
- to providing secure access to data in network systems, including
- MAC, DAC, and RBAC. This course can be used in preparation for the
- 350-701: Implementing and Operating Cisco Security Core
- Technologies (SCOR) certification exam.
SCOR: Network Access & Secure Network Management
In this course, you'll learn about options for the management of
- Cisco Firepower devices, including FMC, FDM, and ASDM. You'll
- explore how AAA can protect access through the device and to the
- device. Next, you'll learn about the RADIUS and TACACS+ security
- protocols, as well as commands you should use to ensure
- authentication to a Cisco device. Finally, you'll learn about
- critical best practices in secure network management for your
- enterprise and the syntax used with SNMP version 3. This course can
- be used in preparation for the 350-701: Implementing and Operating
- Cisco Security Core Technologies (SCOR) certification exam.
SCOR: Configuring and Verifying VPN & IPsec
There are many different styles of site-to-site VPNs possible
- because there are Cisco-centric types, as well as open standard
- designs. In this course, you'll examine a typical configuration of
- a site-to-site VPN, such as the DMVPN configuration and
- verification. Then you'll explore the many types of remote access
- VPN Cisco supports, including having a Cisco ASA provide VPN access
- to remote clients. Finally, you'll learn how to determine if your
- traffic is being protected in your IPsec site-to-site VPN built
- between Cisco devices. This course can be used in preparation for
- the 350-701: Implementing and Operating Cisco Security Core
- Technologies (SCOR) certification exam.
SCOR: Cloud Deployment, Service Models, Responsibilities, & Security
In this course, you'll learn about the cloud in general,
- including the NIST definition of cloud (NIST 800-145) and cloud
- deployment and service models. You'll discover that you don't have
- to sacrifice security when you move to the cloud and explore the
- types of security responsibilities that exist with the cloud and
- the parties that are responsible for them. Finally, you'll learn
- about various cloud security processes and solutions that you
- should be familiar with if the cloud is an important aspect of your
- IT infrastructure, including cloud logging, auditing, and the
- security of workloads. This course can be used in preparation for
- the 350-701: Implementing and Operating Cisco Security Core
- Technologies (SCOR) certification exam.
SCOR: Cisco Firepower, Traffic Management, Identity, & Authentication
In this course, you'll learn about the ASAv, FMCv, and FTDv in
- AWS, as well as how you would register an FTD in the FMC. Next,
- you'll move on to explore the need to deploy web security solutions
- transparently and how to implement this using the Web Cache
- Communication Protocol. You'll also learn how to view the
- implementation with a Cisco ASA. Finally, you'll learn about
- Cisco's Web Security Appliance, how it handles web requests in the
- network, and the importance of identity and authentication on the
- Cisco WSA. This course can be used in preparation for the 350-701:
- Implementing and Operating Cisco Security Core Technologies (SCOR)
- certification exam.
SCOR: Working with ESA, CES, & WSA
Cisco has demonstrated its commitment to securing the enterprise
- with many different solutions that focus on specific needs, such as
- the Email Security Appliance, Cisco Cloud Email Security, and the
- Web Security Appliance. In this course, you'll learn the key facts
- about all three of these solutions. You'll explore how the WSA and
- ESA are impressive appliances when it comes to securing your web
- and e-mail infrastructures and about the components that make up
- these solutions. Even if you're not currently planning on
- implementing a WSA in your enterprise, it can be beneficial to see
- what a typical configuration is like. So next you'll look at the
- options available with the WSA. Finally, you'll learn about the
- steps involved in a typical ESA configuration and verification and
- how the ESA can function for you in the enterprise. This course can
- be used in preparation for the 350-701: Implementing and Operating
- Cisco Security Core Technologies (SCOR) certification exam.
SCOR: Cisco Umbrella & Endpoint Security
When it comes to an IP and DNS-centric approach to network
- security, there is nothing quite like Cisco Umbrella. In this
- course, you'll learn about the Cisco Umbrella solution, including
- how to ensure it is properly configured and verified. Next, you'll
- examine EPP and EDR and their roles in securing network endpoints.
- You'll learn about the importance and uses of Cisco AMP and about a
- variety of other products that can be used to assist with keeping
- your endpoints secure. Finally, you'll explore the Outbreak Control
- functionality of Cisco AMP for Endpoints is the Outbreak Control.
- This course can be used in preparation for the 350-701:
- Implementing and Operating Cisco Security Core Technologies (SCOR)
- certification exam.
SCOR: MDM, MFA, & Endpoint Solutions
Mobile Device Management is widespread and getting more so all
- the time. MDM permits the management and control of all mobile
- devices that make their way to the typical enterprise today and in
- this course you'll learn about MDM as a cloud-based solution. Next,
- you'll look at the three main factors you can use to implement MFA
- and why you might choose some factors over the others. You'll
- examine the use of posture assessment as part of the overall
- security design and the key elements of this approach. Finally,
- you'll learn about the challenges of keeping systems patched, as
- well as various endpoint patching issues and approaches. This
- course can be used in preparation for the 350-701: Implementing and
- Operating Cisco Security Core Technologies (SCOR) certification
- exam.
SCOR: Guest Services, BYOD, 802.1X, & CoA
In lower security environments, there is often a desire to
- permit guest access to the network. These guests might get limited
- Internet access or even access to some of the non-sensitive network
- resources and data. In this course, you'll learn about the Identity
- Service Engine, which is the component in the Cisco security
- portfolio that can make this access seamless to configure and
- implement. You'll also learn about guest access and BYOD for the
- network. Next, you'll move on to examine the use of 802.1X in high
- security enterprises to ensure that each network user is
- authenticated and then authorized for their network and resource
- access. You'll also look at related technologies like MAB and
- WebAuth. Finally, you'll explore the RADIUS Change of Authorization
- feature, which can be critical for certain network security
- functions. This course can be used in preparation for the 350-701:
- Implementing and Operating Cisco Security Core Technologies (SCOR)
- certification exam.
SCOR: Device Compliance, Exfiltration, Telemetry, & Security Products
In this course, you'll learn how device compliance and
- application control can be achieved using Cisco products. You'll
- explore why data exfiltration is one of the central concerns for
- security professionals. Next, you'll learn about network telemetry
- and model-driven telemetry and their increasing popularity in the
- industry. You'll also examine an example of how you might use
- telemetry in the Cisco network. Finally, you'll learn about the
- impressive number of security technologies in the Cisco solution
- portfolio, broken down by category and individual products in each
- category. This course can be used in preparation for the 350-701:
- Implementing and Operating Cisco Security Core Technologies (SCOR)
- certification exam.
Course options
We offer several optional training products to enhance your learning experience. If you are planning to use our training course in preperation for an official exam then whe highly recommend using these optional training products to ensure an optimal learning experience. Sometimes there is only a practice exam or/and practice lab available.
Optional practice exam (trial exam)
To supplement this training course you may add a special practice exam. This practice exam comprises a number of trial exams which are very similar to the real exam, both in terms of form and content. This is the ultimate way to test whether you are ready for the exam.
Optional practice lab
To supplement this training course you may add a special practice lab. You perform the tasks on real hardware and/or software applicable to your Lab. The labs are fully hosted in our cloud. The only thing you need to use our practice labs is a web browser. In the LiveLab environment you will find exercises which you can start immediately. The lab enviromentconsist of complete networks containing for example, clients, servers,etc. This is the ultimate way to gain extensive hands-on experience.
Sign In
WHY_ICTTRAININGEN
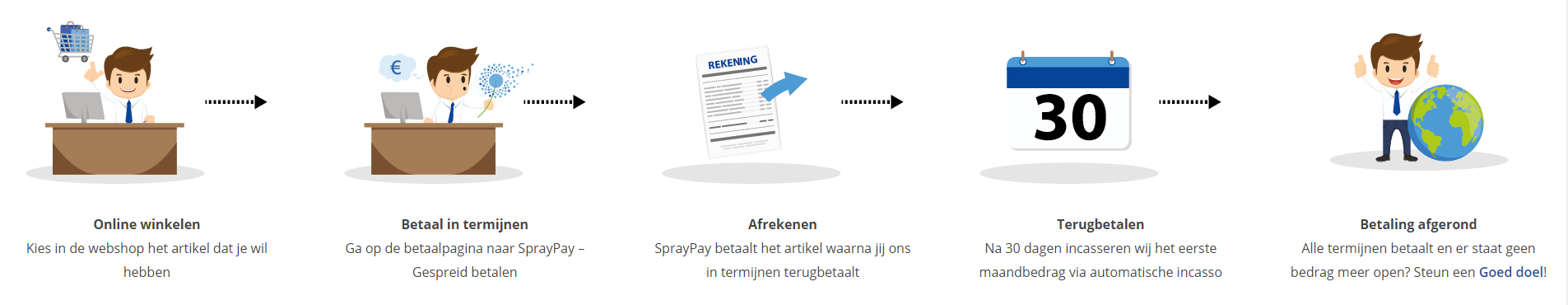
Via ons opleidingsconcept bespaar je tot 80% op trainingen
Start met leren wanneer je wilt. Je bepaalt zelf het gewenste tempo
Spar met medecursisten en profileer je als autoriteit in je vakgebied.
Ontvang na succesvolle afronding van je cursus het officiële certificaat van deelname van Icttrainingen.nl
Krijg inzicht in uitgebreide voortgangsinformatie van jezelf of je medewerkers
Kennis opdoen met interactieve e-learning en uitgebreide praktijkopdrachten door gecertificeerde docenten
Orderproces
Once we have processed your order and payment, we will give you access to your courses. If you still have any questions about our ordering process, please refer to the button below.
read more about the order process
Een zakelijk account aanmaken
Wanneer u besteld namens uw bedrijf doet u er goed aan om aan zakelijk account bij ons aan te maken. Tijdens het registratieproces kunt u hiervoor kiezen. U heeft vervolgens de mogelijkheden om de bedrijfsgegevens in te voeren, een referentie en een afwijkend factuuradres toe te voegen.
Betaalmogelijkheden
U heeft bij ons diverse betaalmogelijkheden. Bij alle betaalopties ontvangt u sowieso een factuur na de bestelling. Gaat uw werkgever betalen, dan kiest u voor betaling per factuur.

Cursisten aanmaken
Als u een zakelijk account heeft aangemaakt dan heeft u de optie om cursisten/medewerkers aan te maken onder uw account. Als u dus meerdere trainingen koopt, kunt u cursisten aanmaken en deze vervolgens uitdelen aan uw collega’s. De cursisten krijgen een e-mail met inloggegevens wanneer zij worden aangemaakt en wanneer zij een training hebben gekregen.
Voortgangsinformatie
Met een zakelijk account bent u automatisch beheerder van uw organisatie en kunt u naast cursisten ook managers aanmaken. Beheerders en managers kunnen tevens voortgang inzien van alle cursisten binnen uw organisatie.
What is included?
| Certificate of participation | Yes |
| Monitor Progress | Yes |
| Award Winning E-learning | Yes |
| Mobile ready | Yes |
| Sharing knowledge | Unlimited access to our IT professionals community |
| Study advice | Our consultants are here for you to advice about your study career and options |
| Study materials | Certified teachers with in depth knowledge about the subject. |
| Service | World's best service |
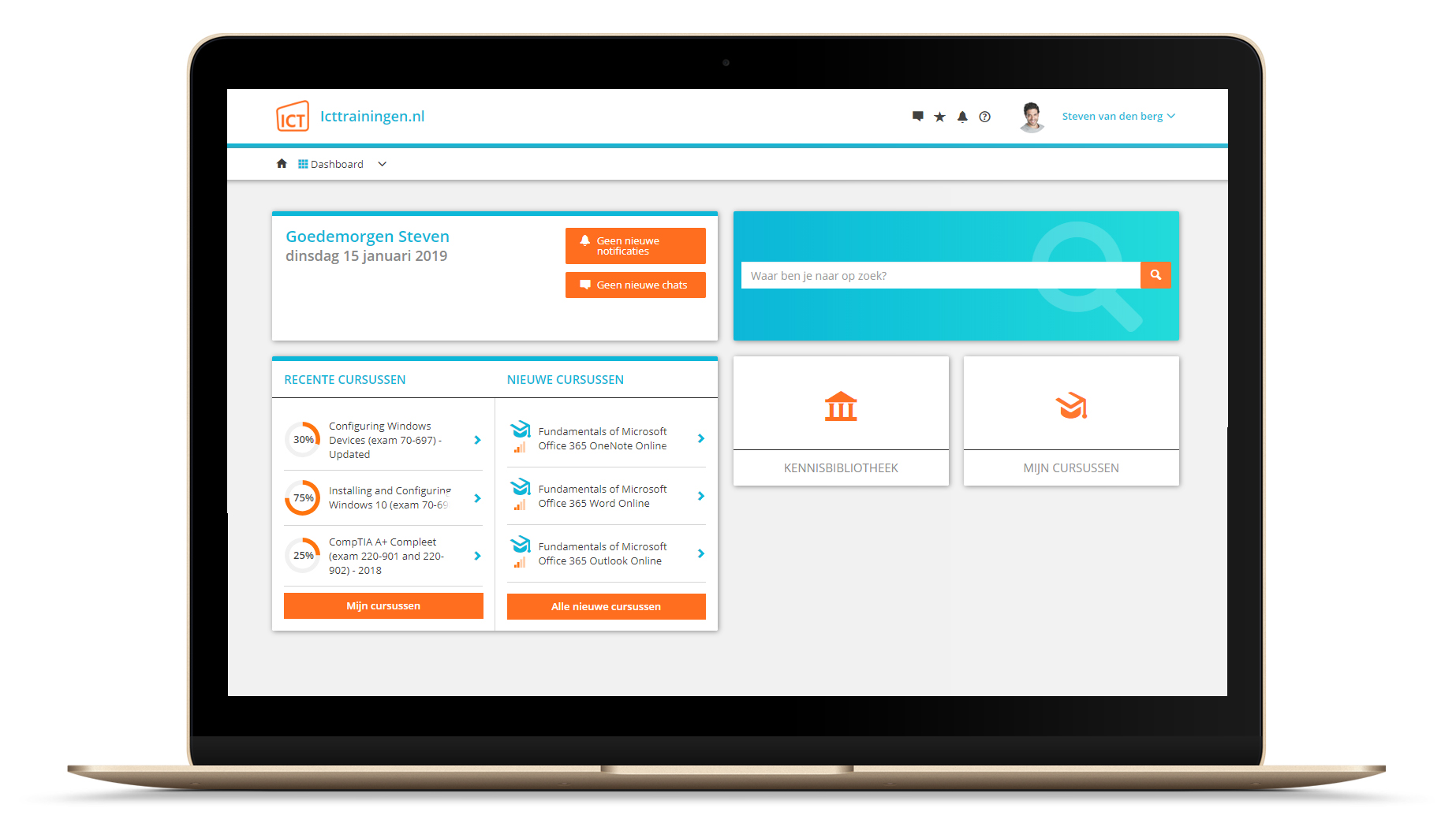
Platform
Na bestelling van je training krijg je toegang tot ons innovatieve leerplatform. Hier vind je al je gekochte (of gevolgde) trainingen, kan je eventueel cursisten aanmaken en krijg je toegang tot uitgebreide voortgangsinformatie.
FAQ
Niet gevonden wat je zocht? Bekijk alle vragen of neem contact op.