Course: OWASP Top 10
duration: 18 hours |
Language: English (US) |
access duration: 180 days |

Details
In this course, you’ll learn all about the OWASP Top 10. This is a standard awareness document for developers and web application security. The most critical security risks to web applications are summarized in it and in this course you’ll learn how to recognize and mitigate them. Next6 to that you will learn to:
- harden resource access to mitigate broken access control attacks;
- protect sensitive data with security controls and classify and encrypt data at rest;
- identify and mitigate web app injection attacks;
- ensure that the design of a web application includes business requirements and related security controls;
- detect security misconfigurations and deploy solutions to rectify weaknesses;
- recognize the importance of using only trusted third-party APIs and software components during application development;
- discover and mitigate authentication vulnerabilities using various tools;
- ensure the integrity of software code, dependencies, and resultant;
- ensure that monitoring is deployed correctly and the timely detection of past security breaches and security incidents in the midst of occurring
- mitigate Cross-Site Request Forgery and Server-Side Request Forgery attacks.
Result
After completing this course, you'll know how to handle the OWASP top 10 risks:
- Broken Access Control
- Cryptographic Failures
- Injection
- Insecure Design
- Security Misconfiguration
- Vulnerable & Outdated Components
- Identification & Authentication Failures
- Software & Data Integrity Failures
- Security Logging & Monitoring Failures
- Server-side Request Forgery (SSRF)
Prerequisites
No formal prerequisites. However, some prior knowledge of the topic is highly recommended.
Target audience
Security Specialist
Content
OWASP Top 10
OWASP Top 10: Securing Web Applications
- Web applications are ubiquitous in today's computing world, and
- many software development tools are available to help with secure
- web app creation. In this course, examine different software
- development tools and explore server-side and client-side code.
- Next, learn how to scan web apps for vulnerabilities using OWASP
- ZAP and Burp Suite, write secure code, and enable the
- Metasploitable intentionally vulnerable web app virtual machine.
- Finally, compare the different types of software testing
- methodologies, learn the difference between vulnerability scanning
- and penetration testing, and discover how web application firewalls
- (WAFs) protect web apps from common attacks. Upon completion,
- you'll be able to recognize the key components of secure web app
- creation and the purpose of the Open Web Application Security
- Project (OWASP).
OWASP Top 10: A01:2021-Broken Access Control
Resource authorization occurs after successful authentication.
- Resources include objects such as files, folders, web apps, storage
- accounts, virtual machines, and more. In this course, learn about
- various resource access control models, including mandatory (MAC),
- discretionary (DAC), role-based (RBAC), and attribute-based access
- control (ABAC). Next, examine how broken access control attacks
- occur and how HTTP requests and responses interact with web
- applications. Discover how to set file system permissions in
- Windows and Linux, assign permissions to code, and digitally sign a
- PowerShell script. Finally, explore identity federation and how to
- execute and mitigate broken access control attacks. Upon
- completion, you'll be able to harden resource access to mitigate
- broken access control attacks.
OWASP Top 10: A02:2021-Cryptographic Failures
Data is one of the most valuable assets to an organization and
- must be protected in accordance with applicable laws, regulations,
- and security standards. In this course, learn about cryptographic
- failure attacks that compromise sensitive data and how to classify
- sensitive data. Next, examine how to hash files in Windows and
- Linux and encrypt files for Windows devices. Then, explore the
- public key infrastructure (PKI) hierarchy and learn how to use a
- certificate to secure a web application with HTTPS. Finally, learn
- how to configure IPsec, encrypt cloud storage, and mitigate
- sensitive data attacks. Upon completion, you'll be able to protect
- sensitive data with security controls and classify and encrypt data
- at rest.
OWASP Top 10: A03:2021-Injection
Many web applications accept input from either external data
- sources or app users. In this course, learn about the types of
- injection attacks and how malicious users submit malicious code or
- commands to a web app for execution by the web server stack. Next,
- practice testing a web app for injection vulnerabilities using the
- OWASP ZAP tool, setting low security for a vulnerable web app tool,
- and executing injection attacks against a web app. Finally,
- discover how to mitigate injection attacks using input validation
- and input sanitization. Upon completion, you'll be able to identify
- and mitigate web app injection attacks.
OWASP Top 10: A04:2021-Insecure Design
Today's web applications combine software code and resultant
- data, with the trustworthiness of both resulting in a secure
- trusted application. There are many planning strategies and tools
- that can ensure software and data integrity. In this course,
- explore IT supply chain security, how to deploy Linux updates, and
- how to configure a Windows Server Update Services (WSUS) host.
- Next, examine object-oriented programming (OOP) and how it is
- related to insecure deserialization attacks. Finally, learn how to
- use the OWASP Dependency-Check tool to verify that publicly
- disclosed vulnerabilities are not present in a project's
- dependencies. Upon completion, you'll be able to ensure that the
- design of a web application includes business requirements and
- related security controls.
OWASP Top 10: A05:2021-Security Misconfiguration
Modern on-premises and cloud networks consist of many types of
- network devices, hosts, and services. Each of these must be
- configured and monitored to ensure continued compliance with
- organizational security policies. In this course, learn about
- security misconfiguration attack criteria, including using default
- credentials, leaving unnecessary services running, and exposing
- services unnecessarily to the Internet. Next, explore application
- container management, including how to pull containers from Docker
- Hub and start them. Finally, examine how containers relate to
- security, how to harden security settings through Group Policy, and
- how to manage software updates on-premises and in the cloud. Upon
- completion, you'll be able to detect security misconfigurations and
- deploy solutions to rectify weaknesses.
OWASP Top 10: A06:2021-Vulnerable & Outdated Components
Software developers often use existing third-party APIs and
- software components. This reduces development time and the time to
- market for software products. In this course, learn about trusted
- APIs and components, including when they are used, how developers
- must truly understand how these items work, and how they must be
- kept up to date. Next, examine the Heartbleed Bug and how to view
- components in Microsoft Visual Studio. Finally, discover how
- security must apply to all aspects of continuous integration and
- continuous delivery (CI/CD) and learn how to search the Shodan
- website for vulnerable devices and apps. Upon completion, you'll be
- able to recognize the importance of using only trusted third-party
- APIs and software components during application development.
OWASP Top 10: A07:2021-Identification & Authentication Failures
Hardening user and device authentication can go a long way in
- securing web applications. In this course, learn the difference
- between authentication and authorization and how they relate to web
- application security. Next, explore how to hash and encrypt user
- credentials and harden user accounts through Microsoft Group Policy
- and practice using freely available tools to crack user credentials
- in various ways, including the Hydra tool, Burp Suite, and John the
- Ripper. Finally, learn how to enable user multi-factor
- authentication and conditional access policies, as well as how to
- mitigate weak authentication. Upon completion, you'll be able to
- recognize how to discover and mitigate authentication
- vulnerabilities using various tools.
OWASP Top 10: A08:2021-Software & Data Integrity Failures
Today's web applications combine software code and resultant
- data, with the trustworthiness of both resulting in a secure and
- trusted application. There are many planning strategies and tools
- that can ensure software and data integrity. In this course, learn
- about IT supply chain security, deploying Linux updates, and
- configuring a Windows Server Update Services (WSUS) host. Next,
- explore object-oriented programming (OOP) and how it is related to
- insecure deserialization attacks. Finally, practice ensuring file
- integrity using file hashing in Windows and Linux and using the
- OWASP Dependency-Check tool to verify that publicly disclosed
- vulnerabilities are not present in a project's dependencies. Upon
- completion, you'll be able to ensure the integrity of software
- code, dependencies, and resultant data.
OWASP Top 10: A09:2021-Security Logging & Monitoring Failures
Modern web applications can consist of many components which are
- often running within application containers. Each component must be
- monitored to detect intrusions. In this course, learn how
- monitoring can be enabled in Linux on individual hosts, Windows,
- and cloud computing environments. Next, explore how to forward log
- entries to a central logging host in Linux and Windows, monitor
- cloud-based web application performance, and download and configure
- the Snort IDS by creating IDS rules. Finally, practice analyzing
- packet captures for suspicious activity and mitigating monitoring
- deficiencies. Upon completion, you'll be able to ensure that
- monitoring is deployed correctly and the timely detection of past
- security breaches and security incidents in the midst of
- occurring.
OWASP Top 10: A10:2021-Server-side Request Forgery (SSRF)
URLs are endpoints for web services that can be accessed
- remotely. Server-Side Request Forgery (SSRF) attacks target servers
- and result from attackers leveraging URLs and vulnerable web
- applications to access sensitive data. Cross-Site Request Forgery
- (CSRF) attacks target client devices and perform unauthorized
- actions using authenticated user sessions with web services. In
- this course, learn about SSRFs. Next, discover how to scan a
- network for HTTP hosts using Nmap, execute a Cross-Site Request
- Forgery (CSRF) attack, and run a Denial of Service (DoS) attack
- against a web server. Finally, practice mitigating controls for
- SSRFs. Upon completion, you'll be able to mitigate Cross-Site
- Request Forgery and Server-Side Request Forgery attacks.
Course options
We offer several optional training products to enhance your learning experience. If you are planning to use our training course in preperation for an official exam then whe highly recommend using these optional training products to ensure an optimal learning experience. Sometimes there is only a practice exam or/and practice lab available.
Optional practice exam (trial exam)
To supplement this training course you may add a special practice exam. This practice exam comprises a number of trial exams which are very similar to the real exam, both in terms of form and content. This is the ultimate way to test whether you are ready for the exam.
Optional practice lab
To supplement this training course you may add a special practice lab. You perform the tasks on real hardware and/or software applicable to your Lab. The labs are fully hosted in our cloud. The only thing you need to use our practice labs is a web browser. In the LiveLab environment you will find exercises which you can start immediately. The lab enviromentconsist of complete networks containing for example, clients, servers,etc. This is the ultimate way to gain extensive hands-on experience.
Sign In
WHY_ICTTRAININGEN
Via ons opleidingsconcept bespaar je tot 80% op trainingen
Start met leren wanneer je wilt. Je bepaalt zelf het gewenste tempo
Spar met medecursisten en profileer je als autoriteit in je vakgebied.
Ontvang na succesvolle afronding van je cursus het officiële certificaat van deelname van Icttrainingen.nl
Krijg inzicht in uitgebreide voortgangsinformatie van jezelf of je medewerkers
Kennis opdoen met interactieve e-learning en uitgebreide praktijkopdrachten door gecertificeerde docenten
Orderproces
Once we have processed your order and payment, we will give you access to your courses. If you still have any questions about our ordering process, please refer to the button below.
read more about the order process
Een zakelijk account aanmaken
Wanneer u besteld namens uw bedrijf doet u er goed aan om aan zakelijk account bij ons aan te maken. Tijdens het registratieproces kunt u hiervoor kiezen. U heeft vervolgens de mogelijkheden om de bedrijfsgegevens in te voeren, een referentie en een afwijkend factuuradres toe te voegen.
Betaalmogelijkheden
U heeft bij ons diverse betaalmogelijkheden. Bij alle betaalopties ontvangt u sowieso een factuur na de bestelling. Gaat uw werkgever betalen, dan kiest u voor betaling per factuur.

Cursisten aanmaken
Als u een zakelijk account heeft aangemaakt dan heeft u de optie om cursisten/medewerkers aan te maken onder uw account. Als u dus meerdere trainingen koopt, kunt u cursisten aanmaken en deze vervolgens uitdelen aan uw collega’s. De cursisten krijgen een e-mail met inloggegevens wanneer zij worden aangemaakt en wanneer zij een training hebben gekregen.
Voortgangsinformatie
Met een zakelijk account bent u automatisch beheerder van uw organisatie en kunt u naast cursisten ook managers aanmaken. Beheerders en managers kunnen tevens voortgang inzien van alle cursisten binnen uw organisatie.
What is included?
| Certificate of participation | Yes |
| Monitor Progress | Yes |
| Award Winning E-learning | Yes |
| Mobile ready | Yes |
| Sharing knowledge | Unlimited access to our IT professionals community |
| Study advice | Our consultants are here for you to advice about your study career and options |
| Study materials | Certified teachers with in depth knowledge about the subject. |
| Service | World's best service |
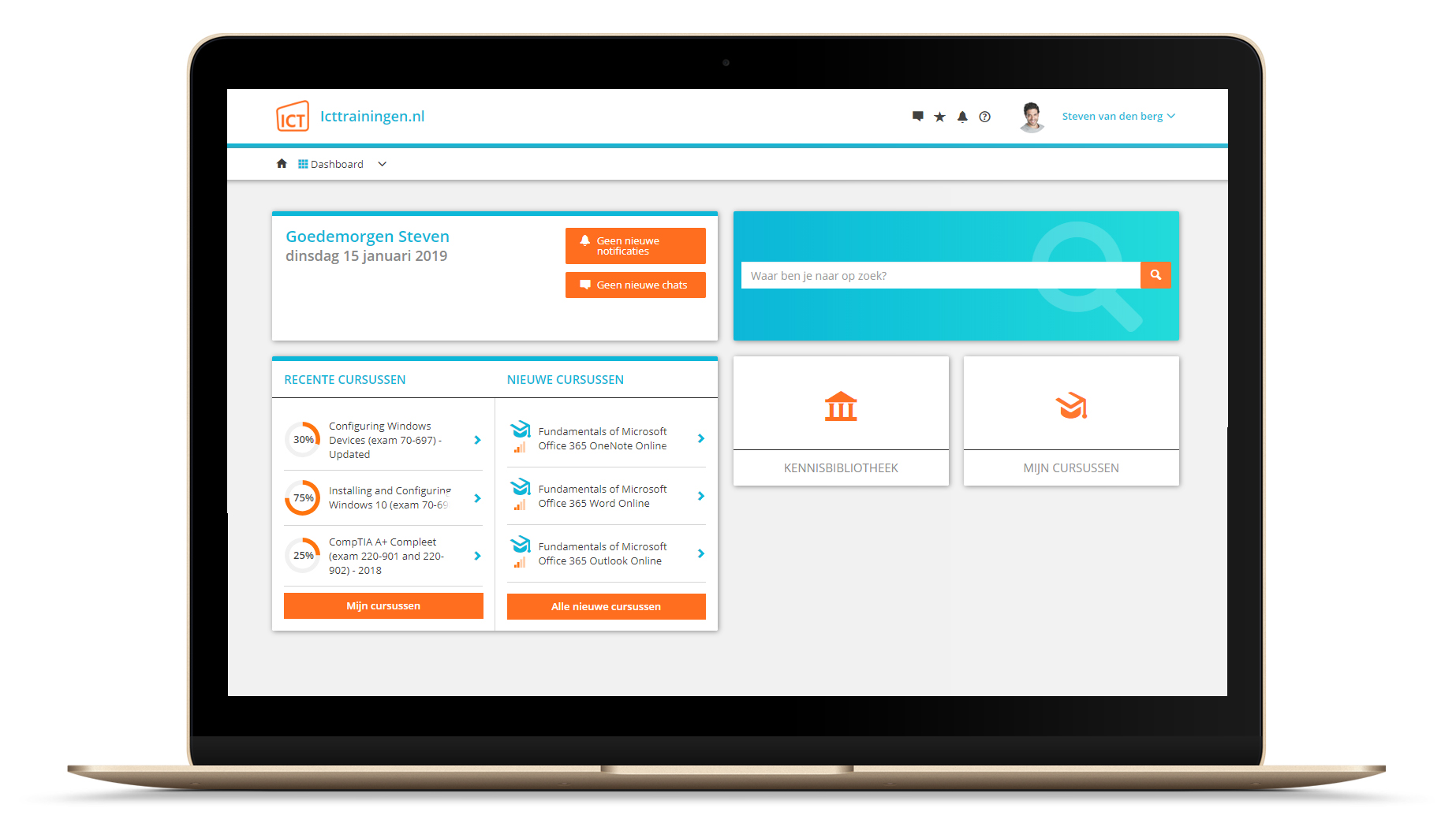
Platform
Na bestelling van je training krijg je toegang tot ons innovatieve leerplatform. Hier vind je al je gekochte (of gevolgde) trainingen, kan je eventueel cursisten aanmaken en krijg je toegang tot uitgebreide voortgangsinformatie.
FAQ
Niet gevonden wat je zocht? Bekijk alle vragen of neem contact op.