Practice Lab CISSP: Certified Information Systems Security Practitioner
duration: 25 hours |
access duration: 180 days |

Details
Through this Practice Lab focused on CISSP exam Certified Information Systems Security Practitioner, you will receive hands-on experience regarding security. By performing tasks in a real network environment, you will improve your practical kwowledge and skills on the various exam subjects. You will perform practical exercises regarding security, Risk Management, Asset Security, Security Engineering, Communcations and Network Security, Security Assessment and Testing, Software Development security and far more.
Result
You have extensive independent experience with regards Security and you are prepared and familiar with the objectives and competencies by the ISC2 CISSP certificate.
Prerequisites
You have successfully finished a training course for the certification exam this lab helps you to prepare for. A training course for this lab is available through us.
Target audience
Security Specialist
Content
Practice Lab CISSP: Certified Information Systems Security Practitioner
Manage Role-based Security
- Introduction
- Exercise 1 - Manage Role-based Security
- Summary
Compliance Patching
- Introduction
- Exercise 1 - Install and Configure WSUS
- Exercise 2 - WSUS Server Certificates Security
- Exercise 3 - Create Computer Groups for WSUS
- Exercise 4 - Configure GPO Policy for WSUS
- Summary
Introduction to CISSP
- Introduction
- Supporting Lab Material - The 8 Domains of CISSP
- Summary
SCCM Configuration Items and Baselines
- Introduction
- Exercise 1 - Create Windows Configuration Items for Compliance Settings
- Exercise 2 - Create Configuration Baseline and Deploy the Baseline
- Exercise 3 - Import Configuration Data in SCCM 2012
- Summary
Implement OpenPGP
- Introduction
- Exercise 1 - Installation of OpenPGP
- Exercise 2 - OpenPGP Certificate Creation and Distribution
- Exercise 3 - OpenPGP Signing and Importation
- Exercise 4 - OpenPGP Verification, Encryption and Decryption
- Summary
Configuring IPtables
- Introduction
- Exercise 1 - Configuring IPtables
- Summary
Managing Remote Desktop
- Introduction
- Exercise 1 - Working with RDP
- Exercise 2 - Administering Windows with PowerShell Remoting
- Summary
Configure and Verify IPv4 and IPv6 Access Lists for Traffic Filtering
- Introduction
- Exercise 1 - Configuring Standard and Extended Access Lists using IPv4
- Exercise 2 - Configuring Named Access Lists Using IPv4
- Exercise 3 - Creating Access-Lists in IPv6
- Summary
Upgrading and Securing SSH Connection
- Introduction
- Exercise 1 - Connecting to Kali
- Exercise 2 - Upgrading OpenSSH
- Exercise 3 - Adding Sudo User
- Exercise 4 - Regenerate SSH Keys to Avoid MITM Attacks
- Exercise 5- Change the MOTD (Message of the Day)
- Exercise 6- Change the SSH Port for Safety
- Summary
Configuring and Securing IIS
- Introduction
- Exercise 1 - IIS Setup
- Exercise 2 - IIS Platform Tour
- Exercise 3 - Inetpub Configuration
- Exercise 4 - IIS Configuration and Security Practices
- Summary
Security and Risk Management
- Introduction
- Supporting Lab Material - Security and Risk Management Part 1
- Supporting Lab Material - Security and Risk Management Part 2
- Summary
Scanning and Remediating Vulnerabilities with OpenVAS
- Introduction
- Exercise 1 - Connecting to Kali
- Exercise 2 - OpenVAS Scanning
- Exercise 3 - Securing Active Directory Access LDAP
- Exercise 4 - Validating Security Changes with OpenVAS
- Summary
Implement SSL VPN using ASA Device Manager
- Introduction
- Exercise 1 - Implement a Clientless SSL VPN using the Cisco ASA Device Manager
- Exercise 2 - Implement AnyConnect using the Cisco ASA Device Manager
- Summary
Bitlocker on Portable Media
- Introduction
- Exercise 1 - Configure Bitlocker on Portable Media
- Summary
Installing Kali
- Introduction
- Exercise 1 - Installing Kali to Hyper-V
- Summary
Installation and Verification of Snort
- Introduction
- Exercise 1 - Installation of Assistance Programs
- Exercise 2 - Configuring Snort
- Exercise 3 - Snort Verification and Results
- Summary
DVWA - Manual SQL Injection and Password Cracking
- Introduction
- Exercise 1 - DVWA Usage
- Exercise 2 - Performing an SQL Injection Attack
- Exercise 3 - Password Cracking with John
- Summary
Implement Backup and Recovery
- Introduction
- Exercise 1 - View Disk allocation Information to Review Storage Pool Data
- Exercise 2 - Create a Protection Group, Add Members and Client Computers to a Protection Group
- Summary
Windows Command Line Tools
- Introduction
- Exercise 1 - IPconfig
- Exercise 2 - Netstat
- Exercise 3 - Ping
- Exercise 4 - Tracert and Route
- Exercise 5 - ARP and Whoami
- Summary
Administering and Deploying Endpoint Protection
- Introduction
- Exercise 1 - Installing an Endpoint Protection Site System Role
- Exercise 2 - Configure Definition Updates for Endpoint Protection
- Exercise 3 - Create and Deploy Antimalware Policies for Endpoint Protection
- Exercise 4 - Configure Custom Client Settings for Endpoint Protection
- Exercise 5 - Provision Endpoint Protection
- Summary
Passive Topology Discovery
- Introduction
- Exercise 1 - Packet Capture with Wireshark
- Exercise 2 - Output Logs
- Exercise 3 - Packet Analysis Part 1
- Exercise 4 - Packet Analysis Part 2
- Summary
Encryption and Hashing
- Introduction
- Exercise 1 - Cryptographic Basics
- Exercise 2 - Comparing Hashing Algorithms
- Exercise 3 - Comparing Hash Values
- Summary
Configuring MBSA Scanner
- Introduction
- Exercise 1 - Introduction to Microsoft Baseline Security Analyser
- Exercise 2 - Implementing Recommendations
- Exercise 3 - Saving Microsoft Security Baseline Analyzer Reports
- Exercise 4 - Reviewing Configuration Changes
- Summary
Two factor Authenication with SSH
- Introduction
- Exercise 1 - Connecting to Kali
- Exercise 2 - Configure Google Authenticator
- Summary
Course options
We offer several optional training products to enhance your learning experience. If you are planning to use our training course in preperation for an official exam then whe highly recommend using these optional training products to ensure an optimal learning experience. Sometimes there is only a practice exam or/and practice lab available.
Optional practice exam (trial exam)
To supplement this training course you may add a special practice exam. This practice exam comprises a number of trial exams which are very similar to the real exam, both in terms of form and content. This is the ultimate way to test whether you are ready for the exam.
Optional practice lab
To supplement this training course you may add a special practice lab. You perform the tasks on real hardware and/or software applicable to your Lab. The labs are fully hosted in our cloud. The only thing you need to use our practice labs is a web browser. In the LiveLab environment you will find exercises which you can start immediately. The lab enviromentconsist of complete networks containing for example, clients, servers,etc. This is the ultimate way to gain extensive hands-on experience.
Sign In
WHY_ICTTRAININGEN
Via ons opleidingsconcept bespaar je tot 80% op trainingen
Start met leren wanneer je wilt. Je bepaalt zelf het gewenste tempo
Spar met medecursisten en profileer je als autoriteit in je vakgebied.
Ontvang na succesvolle afronding van je cursus het officiële certificaat van deelname van Icttrainingen.nl
Krijg inzicht in uitgebreide voortgangsinformatie van jezelf of je medewerkers
Kennis opdoen met interactieve e-learning en uitgebreide praktijkopdrachten door gecertificeerde docenten
Orderproces
Once we have processed your order and payment, we will give you access to your courses. If you still have any questions about our ordering process, please refer to the button below.
read more about the order process
Een zakelijk account aanmaken
Wanneer u besteld namens uw bedrijf doet u er goed aan om aan zakelijk account bij ons aan te maken. Tijdens het registratieproces kunt u hiervoor kiezen. U heeft vervolgens de mogelijkheden om de bedrijfsgegevens in te voeren, een referentie en een afwijkend factuuradres toe te voegen.
Betaalmogelijkheden
U heeft bij ons diverse betaalmogelijkheden. Bij alle betaalopties ontvangt u sowieso een factuur na de bestelling. Gaat uw werkgever betalen, dan kiest u voor betaling per factuur.

Cursisten aanmaken
Als u een zakelijk account heeft aangemaakt dan heeft u de optie om cursisten/medewerkers aan te maken onder uw account. Als u dus meerdere trainingen koopt, kunt u cursisten aanmaken en deze vervolgens uitdelen aan uw collega’s. De cursisten krijgen een e-mail met inloggegevens wanneer zij worden aangemaakt en wanneer zij een training hebben gekregen.
Voortgangsinformatie
Met een zakelijk account bent u automatisch beheerder van uw organisatie en kunt u naast cursisten ook managers aanmaken. Beheerders en managers kunnen tevens voortgang inzien van alle cursisten binnen uw organisatie.
What is included?
| Certificate of participation | No |
| Monitor Progress | Yes |
| Examination possible | Yes |
| Mobile ready | Yes |
| Sharing knowledge | Unlimited access to our IT professionals community |
| Study advice | Our consultants are here for you to advice about your study career and options |
| Study materials | Certified teachers with in depth knowledge about the subject. |
| Service | World's best service |
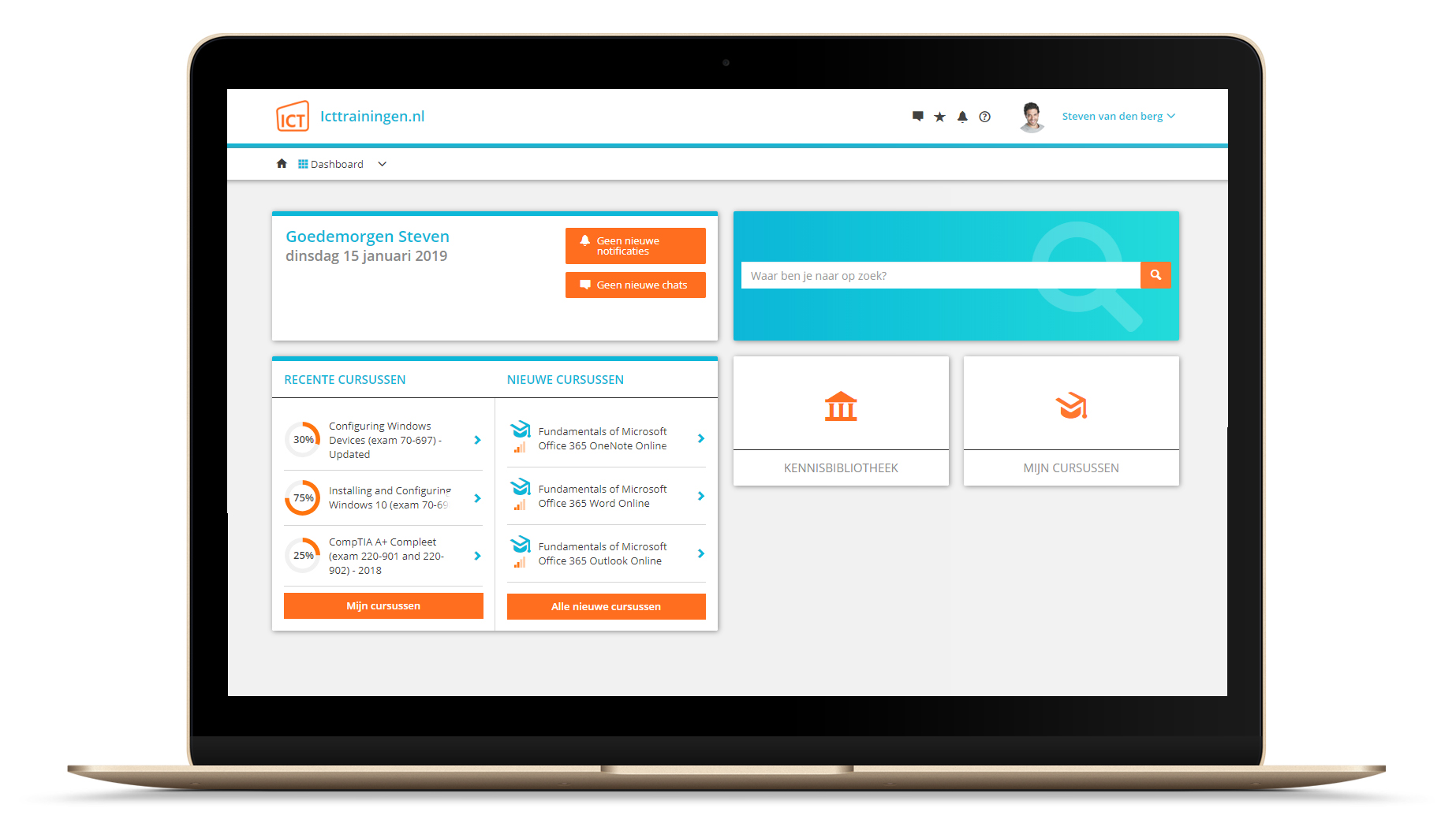
Platform
Na bestelling van je training krijg je toegang tot ons innovatieve leerplatform. Hier vind je al je gekochte (of gevolgde) trainingen, kan je eventueel cursisten aanmaken en krijg je toegang tot uitgebreide voortgangsinformatie.
FAQ
Niet gevonden wat je zocht? Bekijk alle vragen of neem contact op.