Develop yourself from Penetration Tester to SecOps Engineer (incl. guidance)
duration: 46 hours |
Language: English (US) |
access duration: 365 days |

Details
Are you interested in both IT security and IT operations? Do you want to contribute to better security and better operational performance of an organisation? Then maybe a job as SecOps Engineer is for you! The primary goal of SecOps is to reduce process inefficiencies of traditional enterprise security and operations teams by enabling them to share responsibility, processes, tools and information, leading to improved security and operational performance. In this learning path you will explore different roles to develop yourself from Penetration Tester to SecOps Engineer.
When you choose for this learning path, you get:
- access to the training courses and LiveLabs around the roles of Penetration Tester, Incident Response Leader, Ethical Hacker and SecOps Engineer. On top of that you get access to many more training courses, mock exams, bootcamps, e-books and so on.
- Guidance from our Learning and Development Team. Together with you, we will set goals, make a planning and monitor your progress.
Penetration Tester
The first section focuses on the basics of penetration testing, security measures, end-user behaviour, physical and Wi-Fi pen testing, and advanced pen testing techniques.
Incident Response Leader
Next, you'll learn about incident response, preventive troubleshooting, network equipment security, system configuration monitoring, patch management, and regulatory compliance.
Ethical Hacker
In this section you will learn about Ethical Hacking.
SecOps Engineer
Finally, you'll work with SecOps Engineering. You'll learn about secure coding, cloud and IoT security and threat mitigation.
Result
After completing this learning path, you will have developed yourself into a SecOps Engineer.
Prerequisites
You have basic knowledge of penetration testing and ethical hacking.
Target audience
Security Specialist, Tester
Content
Develop yourself from Penetration Tester to SecOps Engineer (incl. guidance)
Penetration Testing Fundamentals
Delve into the world of penetration testing and examine the
- common types of penetration testing and the important role they
- play in protecting your company's assets and networks from exploits
- and attacks. Explore methods for gathering information,
- vulnerability scanning, common exploits and vulnerabilities, and
- methods and techniques for preventing these exploits.
Pen Testing Awareness: Results Management
Security Measures: Implementing Security Controls
Explore the use of security controls with the NIST Cybersecurity Framework. Examine the anatomy of security controls, from common to the advanced and complex. Discover how to test and monitor security controls, including some of the most basic quick win controls for several control types. In addition, control policies within the NIST Cybersecurity Framework, how security controls contribute to the ISO 27002 standard in compliance, risk management scenarios, and how security controls are enforced and implemented are also covered.
Pen Testing: End-user Behavior
Explore the limitations of penetration testing, as well as how end-user behavior affects this process. Discover how human error can cause data breaches and the importance of end-user awareness. Examine tools used to perform user behavior analytics, social engineering attacks and countermeasures, and how to create penetration testing reports.
Physical Penetration Testing
Discover the importance of physical penetration testing and the steps for performing a physical penetration test. Examine lock picking techniques and the benefits of dumpster diving. Finally, explore how to protect sensitive data, penetration testing tools and techniques, and the different types of penetration tests.
Wi-Fi Penetration Testing
Discover how to recognize the vulnerabilities in wireless networks. Examine the tests used to determine if specific vulnerabilities can be exploited in a wireless network and how test results can be used to enhance your company's security policy.
Pen Testing: Advanced Pen Testing Techniques
Explore advanced penetration testing tools and techniques used
- to find vulnerabilities, sniff network traffic, deal with
- cryptography, and crack passwords. Discover the benefits of using
- the Python programming language to build scripts and deliver tools,
- and examine common techniques used to find weaknesses in both Linux
- and Windows-based systems.
Final Exam: Penetration Tester
Final Exam: Penetration Tester will test your knowledge and application of the topics presented throughout the Penetration Tester track of the Skillsoft Aspire Penetration Tester to SecOps Engineer Journey.
Policy & Governance: Incident Response
Discover the importance of an incident response plan, including
- how to draft the plan and engage in incident response. Explore
- different scenarios and what roles are needed to manage an incident
- response team. Examine the notion of the Computer Security Incident
- Response Team and how the team effectively responds to incidents.
- How incident response policies can provide IT governance and
- compliance in today's cyber world and best practices for staying
- compliant with ISO and other compliance standards is also
- covered.
Planning Measures: Incident Response Planning
Explore the process of recovering from security related
- incidents such as malware, data leakage, or stolen equipment.
- Examine how to develop plans, policies, and procedures and how to
- form a team with well defined roles to execute these plans.
- Finally, examine how all these components are coordinated in
- practice when an incident event occurs.
Preemptive Troubleshooting: Concepts & Strategies
Explore preemptive troubleshooting concepts and strategies and
- how they apply to cybersecurity. Discover tools to help assist in
- troubleshooting, such as indicators and threat hunting. Dive into
- scenarios a SOC would typically engage in when troubleshooting
- network issues and system compromise. Examine best practices,
- including spotting weak passwords or hardware and software
- vulnerabilities, and security policies and procedures to keep
- systems secure.
Security Best Practices: Network Appliance Security
Explore security best practices, top security risks, the importance of securing network appliances, and how to secure them. Examine risks and best practices for transitioning to the cloud, traditional infrastructure deficiencies, and how to deal with de-perimeterization problems. Various security architecture models, including the Zero Trust Architecture, are also covered.
Monitoring & Securing System Configuration
In this course, you'll learn how to drive system configuration monitoring using continuous monitoring tools to keep systems secure. You'll explore the concept and importance of monitoring system configuration within an organization for incident response. Next, you'll examine tools and strategies you can use to identify common issues, such as identifying weak passwords or common devices that use default credentials. You'll explore processes for operating and maintaining monitoring systems, including the use of security controls and assessments to ensure the incident response team remains compliant. Finally, you'll discover how to identify and interpret report findings from monitoring result, how to work with a monitoring program for system configuration, and how to recognize monitoring program challenges and possible solutions for incident response.
Security Strategy: Patch Management Strategies
Discover how patch management strategies are an important part of an overall security strategy, beginning with basic patch management concepts and how to prioritize what to patch and when. Examine best practices, what to do when vendor-specific issues occur, and how to get issues patched before they become a threat. Explore various tools and techniques used to patch and harden systems and the process of implementing patches, including automating the process to make things easier for the day-to-day SecOps professional. Look at how to analyze and assess patches before implementation to prevent any unknowns or issues. Finally, how patch management fits into the Agile software development process and how to implement patches in a serverless architecture are also covered.
Regulation Conformance for Incidence Response
Cybersecurity is a growing concern for organizations, especially in government and in private sectors. Policies and regulations that need to be conformed to and practiced in the industry are also important considerations for incident response leaders. Explore regulation conformance for incident response, including how to build and apply a conformance plan in the workplace. Examine industry standards, how to apply techniques in regulation conformance, and how to handle incidents that require specific regulation conformance. Discover how to document incidents following the appropriate standards and how to provide a conformance plan that follows regulations and standards for the organization.
Incident Response Leader
Incident Response Leader Perform tasks commonly completed by Incident Response Leaders tasks such as implementing data governance, deploying software and hardware patches, and implementing monitoring, controls and backups. Then, test your skills by answering assessment questions after responding to an active threat and performing a root cause analysis on an active threat on both a Windows system and a cloud based system. This lab is part of the Incident Response Leader track of the Skillsoft Aspire Penetration Tester to SecOps Engineer journey.
Final Exam: Incident Response Leader
Final Exam: Incident Response Leader will test your knowledge and application of the topics presented throughout the Incident Response Leader track of the Skillsoft Aspire Penetration Tester to SecOps Engineer Journey.
Ethical Hacker: Risk Assessment
Ultimately, ethical hacking is about testing the risk level an
- organization has. In order to perform effective, professional
- ethical hacking, a knowledge of risk is essential. Explore risk
- assessment concepts, including risk calculations, responses, and
- models. Discover how to use the Common Vulnerability Scoring System
- and how to apply risk management concepts and evaluate risk in
- accordance with common standards.
Ethical Hacker: Incident Response
Ethical hacking is a means to avoid incidents and to discover
- them before they are realized. Often, ethical hacking is part of
- the response to an incident, so an understanding of incident
- handling is important for the ethical hacker. Explore the
- foundational concepts of incident response, including incident
- classification, recovery and remediation, and after action
- review.
Ethical Hacker: Security Standards
Ethical hacking is not just random hacking attempts. It is a systematic testing of the target's security. For that reason, an understanding of security standards and formal testing methodologies is critical. Examine key security standards including penetration testing standards.
Ethical Hacker: Secure Technology & Applications
Security devices and software are the technical aspect of
- security. An ethical hacker must be familiar with security
- technology in order to effectively conduct tests of the target
- organization's network. Explore security device and software
- concepts, firewall types and usage, SIEM systems, IDS/IPS,
- antivirus strategies, Windows Firewall, and how to implement
- Snort.
Ethical Hacker: Account Creation
Account management and access control are fundamental to security, and it's vital to understand these technologies as an ethical hacker. Explore account creation concepts, standard access control models, attribute-based access control, and how to design account and access control.
Ethical Hacker: Scanning
One of the early stages in ethical hacking is reconnaissance of the target. Explore various scanning tools and techniques used in ethical hacking, including NMAP, OWASP ZAP, Vega, Shodan, and specialized Google searches.
Ethical Hacker: Hacking Techniques
Ultimately, ethical hacking is about hacking, so the ethical hacker must have some hands-on hacking skills. Explore fundamental hacking techniques, including SQL injection, cross-site scripting, malware, using viruses, DoS attacks, steganography, using Metasploit, and Windows hacking.
Ethical Hacker
- Perform tasks commonly completed by Ethical Hackers such as disaster recovery configuration and testing, digital forensics, and data exfiltration. Then, test your skills by answering assessment questions after scanning websites and conducting SQL injections, as well as employing common hacking techniques to gain access to Windows and Linux machines.
- This lab provides access to tools typically used by Ethical Hackers, including:
- - ownCloud
- - Wireshark
- - Autopsy
- - Vega
- - Nikto
- This lab is part of the Ethical Hacker track of the Skillsoft Aspire Penetration Tester to SecOps Engineer Journey.
Final Exam: Ethical Hacker
Final Exam: Ethical Hacker will test your knowledge and application of the topics presented throughout the Ethical Hacker track of the Skillsoft Aspire Penetration Tester to SecOps Engineer Journey.
SecOps Engineer: System Infrastructure Security
Explore SecOps engineering concepts, including why you should
- harden your infrastructure and operating systems to mitigate
- threats. Discover how to analyze Windows 10 issues, use security
- devices, and implement intrusion detection and prevention systems.
- In addition, Windows Server hardening, proper firewall placement,
- and using and deploying honeypots effectively is covered.
SecOps Engineer: Secure Coding
Discover how to protect your software by applying secure coding
- practices. Explore key concepts, including filtering, validation,
- and the CERT Top 10 Secure Coding Practices. Examine methods for
- securing software deployment and continuous delivery, as well as
- secure software metrics and secure coding with C#, Python, and
- Java.
SecOps Engineer: Security Engineering
Explore cybersecurity engineering concepts, including security modeling techniques and the Security Modeling Language. Discover how to analyze and use security metrics, analyze failures, integrate systems engineering into cybersecurity operations, and apply security requirements engineering techniques.
SecOps Engineer: Cloud & IoT security
Explore cloud and IoT security concepts, including common threats. Examine cloud architecture, types, and uses, as well as how to apply cloud security methods and techniques. Discover how to implement IoT security for a wide range of IoT devices.
SecOps Engineer: Threat Mitigation
Discover how to recognize and analyze common threats, such as malware, denial of service, social engineering, phishing, and insecure protocols. Examine how to integrate your analysis into mitigating these types threats and how to effectively use cyberthreat intelligence resources.
SecOps Engineer
- Perform tasks commonly completed by SecOps Engineers such as configuring intrusion detection and prevention, Windows and network hardening, and creating and monitoring a honeypot. Then, test your skills by answering assessment questions after configuring items to protect against ransomware and denial of service attacks, configure auditing to detect insider threats, and impllement controls to protect insecure and legacy systems.
- This lab provides access to tools typically used by SecOps Engineers, including:
- - OPN SEnse
- - SPLUNK SIEM platform
- - ownCloud
- - FastNetMon DdoS Mitigation
- - Wazuh
- This lab is part of the SecOps Engineer track of the Skillsoft Aspire Penetration Tester to SecOps Engineer Journey.
Final Exam: SecOps Engineer
Final Exam: SecOps Engineer will test your knowledge and application of the topics presented throughout the SecOps Engineer track of the Skillsoft Aspire Penetration Tester to SecOps Engineer Journey.
Course options
We offer several optional training products to enhance your learning experience. If you are planning to use our training course in preperation for an official exam then whe highly recommend using these optional training products to ensure an optimal learning experience. Sometimes there is only a practice exam or/and practice lab available.
Optional practice exam (trial exam)
To supplement this training course you may add a special practice exam. This practice exam comprises a number of trial exams which are very similar to the real exam, both in terms of form and content. This is the ultimate way to test whether you are ready for the exam.
Optional practice lab
To supplement this training course you may add a special practice lab. You perform the tasks on real hardware and/or software applicable to your Lab. The labs are fully hosted in our cloud. The only thing you need to use our practice labs is a web browser. In the LiveLab environment you will find exercises which you can start immediately. The lab enviromentconsist of complete networks containing for example, clients, servers,etc. This is the ultimate way to gain extensive hands-on experience.
Sign In
WHY_ICTTRAININGEN
Via ons opleidingsconcept bespaar je tot 80% op trainingen
Start met leren wanneer je wilt. Je bepaalt zelf het gewenste tempo
Spar met medecursisten en profileer je als autoriteit in je vakgebied.
Ontvang na succesvolle afronding van je cursus het officiële certificaat van deelname van Icttrainingen.nl
Krijg inzicht in uitgebreide voortgangsinformatie van jezelf of je medewerkers
Kennis opdoen met interactieve e-learning en uitgebreide praktijkopdrachten door gecertificeerde docenten
Orderproces
Once we have processed your order and payment, we will give you access to your courses. If you still have any questions about our ordering process, please refer to the button below.
read more about the order process
Een zakelijk account aanmaken
Wanneer u besteld namens uw bedrijf doet u er goed aan om aan zakelijk account bij ons aan te maken. Tijdens het registratieproces kunt u hiervoor kiezen. U heeft vervolgens de mogelijkheden om de bedrijfsgegevens in te voeren, een referentie en een afwijkend factuuradres toe te voegen.
Betaalmogelijkheden
U heeft bij ons diverse betaalmogelijkheden. Bij alle betaalopties ontvangt u sowieso een factuur na de bestelling. Gaat uw werkgever betalen, dan kiest u voor betaling per factuur.

Cursisten aanmaken
Als u een zakelijk account heeft aangemaakt dan heeft u de optie om cursisten/medewerkers aan te maken onder uw account. Als u dus meerdere trainingen koopt, kunt u cursisten aanmaken en deze vervolgens uitdelen aan uw collega’s. De cursisten krijgen een e-mail met inloggegevens wanneer zij worden aangemaakt en wanneer zij een training hebben gekregen.
Voortgangsinformatie
Met een zakelijk account bent u automatisch beheerder van uw organisatie en kunt u naast cursisten ook managers aanmaken. Beheerders en managers kunnen tevens voortgang inzien van alle cursisten binnen uw organisatie.
What is included?
| Certificate of participation | Yes |
| Monitor Progress | Yes |
| Award Winning E-learning | Yes |
| Mobile ready | Yes |
| Sharing knowledge | Unlimited access to our IT professionals community |
| Study advice | Our consultants are here for you to advice about your study career and options |
| Study materials | Certified teachers with in depth knowledge about the subject. |
| Service | World's best service |
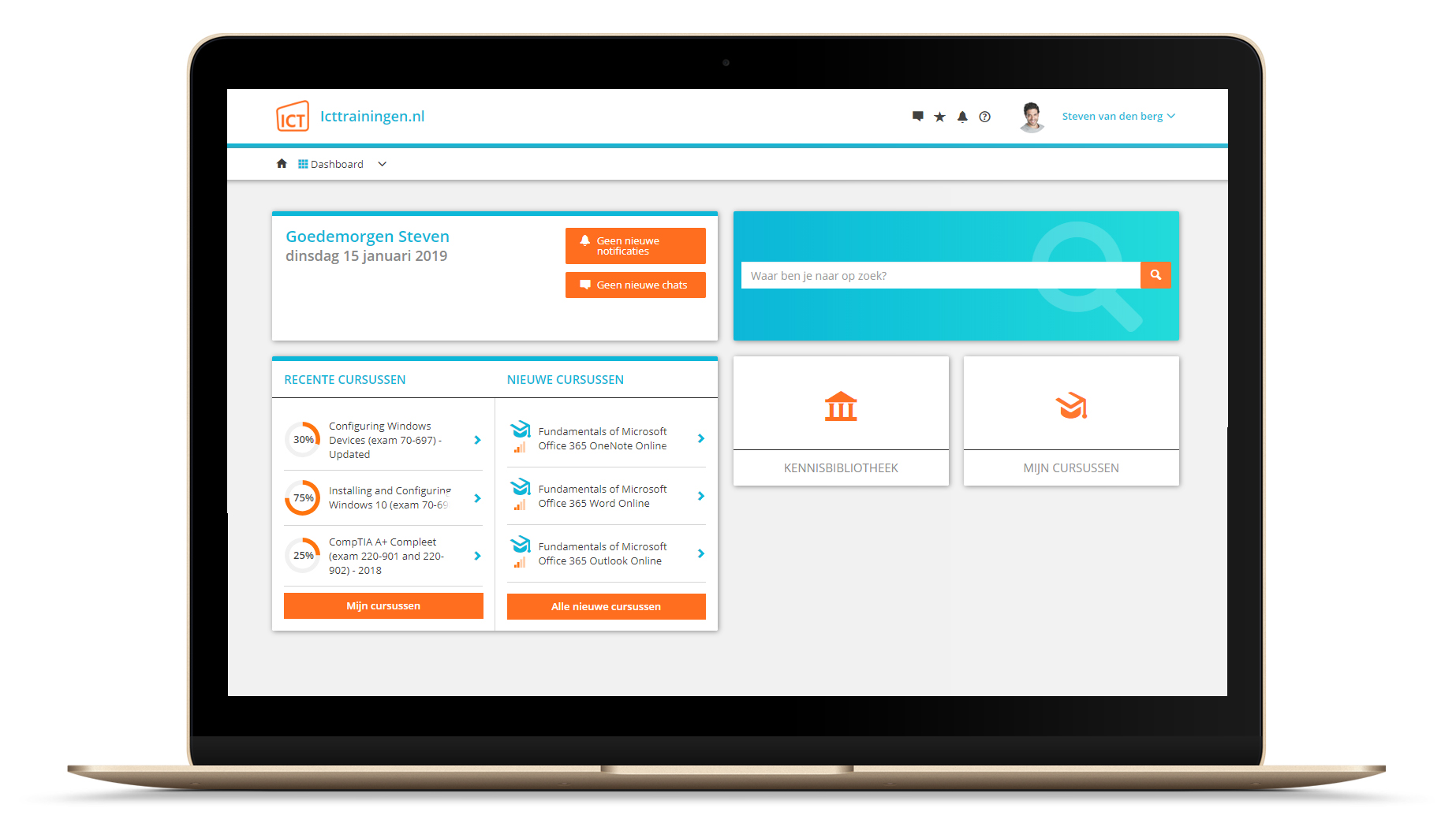
Platform
Na bestelling van je training krijg je toegang tot ons innovatieve leerplatform. Hier vind je al je gekochte (of gevolgde) trainingen, kan je eventueel cursisten aanmaken en krijg je toegang tot uitgebreide voortgangsinformatie.
FAQ
Niet gevonden wat je zocht? Bekijk alle vragen of neem contact op.