Course: Building a SecOps Toolbox
duration: 41 hours |
Language: English (US) |
access duration: 180 days |

Details
This course gives you the background needed to understand essential Cybersecurity tools. You will learn why Cybersecurity Tools (SecTools) organization and planning are important, identify the chief causes of the security breaches, and prescribe which processes and tools were needed to fix each situation.
You will also learn, with industry examples, how to install, set up, and utilize the most common SecTools using common, rapid-start Security Operation (SecOps) platforms like Kali Linux. Finally, you'll explore how Artificial Intelligence (AI) enhances our ability to combat cybersecurity incidents and learn how to implement AI into your SecTools processes.
Result
After completing this course, you'll have gained knowledge of some essential security tools that can help you with threat assessment and dealing with security incidents.
Prerequisites
Basic knowledge of and experience with networking and linux are recommended.
Target audience
Security Specialist
Content
Building a SecOps Toolbox
SecOps Tool Landscape: Intro to Security Tools (SecTools)
Organizations spend money on security controls to protect company assets, but how do they know those assets are protected from hackers? One way is to use the same tools that hackers use and perform security test known as penetration testing or ethical hacking. In this course, explore the purpose of security tools, including their history and the response to modern attacks. Take a look at open-source intelligence tools used to collect information from online sources. Next, investigate the purpose and importance of ethical hacking. Finally, examine the value of building a security toolbox, the different categories of tools, and how to obtain appropriate security tools.
SecOps Tool Landscape: The Kali Linux Security Platform
The Kali Linux operating system comes with many pre-installed security tools. It is a popular choice among penetration testers and its tools can be used to assess the security of network devices and systems. In this course, learn the benefits of Kali Linux and how to download and install it. Next, explore the Kali Linux user interface and work with some of its tools. Finally, discover how to use common tools in Kali for various operations, such as Nmap for port scanning, Hydra for compromising a system, sqlmap for performing SQL injection attacks, and Ophcrack for cracking passwords. Upon completion, you'll be able to recognize the benefits of Kali Linux, download and install it, and use various Kali tools to execute testing tasks.
SecOps Tools and 2021 Security Incidents: Microsoft Exchange Server Data Breach
Cybersecurity professionals are often tasked with studying breaches that have impacted other organizations to protect their assets. This knowledge helps them identify potential threats and understand how threat actors operate in a modern environment. In this course, explore the background of the Microsoft Exchange Server data breach, how it was discovered, and how Microsoft communicated about it. Review different tools that can be used to discover and exploit the vulnerability. Finally, explore how the cybersecurity community responded and how you can patch systems against such a breach. Upon completion of this course, you'll be able to describe the Microsoft Exchange Server data breach and how to detect it, as well as respond if you find a server that could be compromised by the same vulnerability.
SecOps Tools and 2021 Security Incidents: Facebook Data Breach
Cybersecurity professionals will often be tasked with studying breaches that have impacted other organizations to protect their own assets. This knowledge helps in identifying potential threats and understanding how threat actors operate in a modern environment. Begin this course by exploring the background of the Facebook data breach and how it was initially discovered. Then, explore how the data breach happened, and the method used to capture the data. Next, explore different tools that could be used to conduct a similar type of attack. Finally, examine the cybersecurity community's response to the breach and the fallout for Facebook from the event. On completing this course, you will have a better understanding of the Facebook data breach, how to conduct a similar attack, and how such a cybersecurity event can impact an organization.
SecOps Tools and 2021 Security Incidents: Colonial Pipeline
Cybersecurity professionals often will be tasked with studying breaches that have impacted other organizations to protect their own assets. This knowledge helps to identify potential threats and understand how threat actors are operating in a modern environment. Begin this course by exploring the background of the Colonial Pipeline breach and how it was discovered. Then, examine how the data breach happened, focusing on credential harvesting methods typically used to capture login data. Next, investigate the different tools that could be used to conduct a similar type of attack, including Maltego CE, theHarvester, the Social-Engineer Toolkit and Zphisher. Finally, take a look at the cybersecurity community response and cybersecurity implications resulting from the Colonial Pipeline incident. Once you have completed this course, you will be able to use tools to conduct an attack similar to the Colonial Pipeline breach and identify potential threats to other organizations.
SecOps Tools and 2021 Security Incidents: JBS Ransomware Attack
Cybersecurity professionals often will be tasked with studying breaches that have impacted other organizations. This knowledge helps to identify potential threats and understand how threat actors are operating in a modern environment. Explore the background of the JBS ransomware attack and how it was discovered. Then, investigate how the breach happened and examine various vulnerability scanning and exfiltration tools that could be used to conduct this type of attack. Finally, take a look at the cybersecurity community response to the breach and the fallout for JBS Foods from the event. Once you have completed this course you should be familiar with the background of the JBS ransomware attack, how to use tools to conduct a similar type of attack, and how JBS Foods and the Government responded to the breach.
SecOps Tools and 2021 Security Incidents: Kaseya Ransomware Attack
Supply chain attacks are particularly stealthy and have the potential to inflict considerable damage that can have lasting repercussions. Cybersecurity professionals need to proactively monitor traffic to stay ahead of these types of attacks and other potential threats. Begin this course by exploring the background of the Kaseya ransomware attack and how it was discovered. Then, examine what led to the breach and how the attack affected Kaseya's clientele of multiple managed service providers (MSPs) and as a result, many small businesses downstream. Investigate the various tools, like SQL injection, that could be used to conduct this type of attack. Finally, take a look at the cybersecurity community response to the breach and the fallout for Kaseya from the event. Once you have completed this course, you should understand the background of the Kaseya ransomware attack, how to use tools to conduct a similar type of attack, and how Kaseya and the government responded to the breach.
SecOps Tools and 2021 Security Incidents: Log4Shell Exploit
Cybersecurity professionals are often tasked with studying breaches that have impacted other organizations to protect their assets. This knowledge helps identify potential threats and understand how threat actors operate in a modern environment. In this course, we begin by exploring the background of the Log4Shell exploit and how it was discovered. We then explore how the exploit was disclosed and various tools that can be used to scan for the vulnerability. We even look at how to conduct the exploit ourselves. Finally, we discuss the patches and response to the exploit by the open-source community and the long-term political and cybersecurity fallout. Upon completion of this course, you'll be able to describe the tools used to detect and conduct a Log4Shell exploit.
Exploring SecOps Tools: Web Application Hardening via Burp Suite
Burp Suite is a common set of proxy-based tools used for penetration testing and security evaluation of web-based applications. It has become one of the industry-standard toolkits used by information security professionals. Explore the Burp Suite of tools and products and discover common Burp Suite solutions such as application security testing, DevSecOps, compliance, and penetration testing. Find out how Burp Suite can help integrate security into software development and investigate potential limitations and disadvantages of the suite. Learn the Burp Suite installation process and how to navigate the common features of the Burp Suite user interface. Lastly, explore how to perform API security testing and how to scan a website for vulnerabilities using Burp Suite. When you have finished this course, you will be able to confidently use Burp Suite for web application hardening.
Exploring SecOps Tools: Network Scanning Using Nmap
The Network Mapper (Nmap) utility is a free, open-source network discovery and security auditing tool. Nmap is one of the industry's leading network scanning tools and is commonly used to discover hosts and services on a computer network. In this course, you'll explore the history of Nmap, its features and benefits, and the potential limitations and considerations of the Nmap tool. Discover how to download, install, and explore the Nmap utility user interface and how to perform Nmap TCP connect and Nmap stealth scans. Lastly, explore when to use Nmap to perform inverse scans, and discover situations that warrant using Nmap to perform an ACK scan.
Exploring SecOps Tools: Network Packet Manipulation Using Wireshark
The ability to conceptualize a network's structure, capabilities, and events is essential to protecting it. In this course, you'll explore the Wireshark network protocol analyzer and its concepts and capabilities, which can be used to identify and visualize your network components. Discover common scenarios in which to use Wireshark and potential limitations of the Wireshark utility. Explore how to download and install Wireshark and how to perform basic network traffic filtering. Finally, discover how to create a baseline for monitoring, firewall rules, and how to monitor traffic remotely using Wireshark.
Exploring SecOps Tools: Penetration Testing Using Metasploit Framework
Metasploit is an open-source penetration testing framework that can be used by security professionals and ethical hackers to verify vulnerabilities, manage security assessments, and improve security awareness. One of the primary capabilities of Metasploit is the ability to write, test, and execute exploit code. In this course, you'll explore the Metasploit framework, its features, and its capabilities. Discover the Metasploit module types, including exploit, auxiliary, post-exploitation, payload, and no operation payload (NOP) generator, and identify possible disadvantages and limitations of Metasploit. Explore how to download and install Metasploit and discover how to work with modules, exploits, and payloads. Lastly, explore how to execute common Metasploit commands and recognize key steps involved in attacking a system using Metasploit.
Exploring SecOps Tools: Using the Aircrack-ng Suite of Tools
Aircrack-ng is a complete suite of tools commonly used to assess Wi-Fi network security and perform network security hardening. These tools focus primarily on monitoring, attacking, testing, and password cracking. All Aircrack-ng individual utilities are command-line based and allow for maximum scripting utilities. In this course, you will explore the Aircrack-ng suite of tools and discover the individual utilities found within. Compare Aircrack-ng to alternatives including Trackerjacker, Eaphammer, Wifiphisher, Wireshark, Airgeddon, and Acrylic Wi-Fi, and recognize considerations for installing drivers with Aircrack-ng. Discover how to download and install Aircrack-ng and explore how to navigate and execute common commands. Finally, discover how to use Aircrack-ng to crack WEP and WPA/WPA2 passwords and explore command options such as -a, -e, -b, -p, -q, -C, -I.
Exploring SecOps Tools: Port Scanning with Netcat
The Netcat utility is a free and easy-to-use tool that is commonly used to monitor the flow of traffic between systems on a computer network. Netcat has various capabilities, including port scanning, port listening, transferring files, and backdoor enabling. With this course, learn how to use the Netcat utility. Explore the history of the Netcat utility and learn how to download and install the program. Next, work with common Netcat commands and options and examine Netcat features like SSL encryption, traffic redirection, and connection brokering. Finally, learn how to execute basic Netcat commands, perform port scanning, and use Netcat TCP server and client commands. Upon completion, you'll be able to use the Netcat utility to perform port scanning.
Exploring SecOps Tools: Securing Passwords with hashcat
hashcat is a popular password cracking tool which is often used in ethical hacking exercises by penetration testers and sysadmins. It is, however, often also used for illicit purposes by cybercriminals and spies to compromise and breach vulnerabilities. Explore the many features and capabilities of the hashcat tool, and discover the purpose and vulnerabilities password hashes present. Explore the characteristics of the core hashcat attack modes that include dictionary attacks, combinator attacks, brute-force attacks, hybrid attacks, and association attacks. Explore how to download and install hashcat and discover techniques to crack passcodes. Lastly, explore requirements for building a capable password cracking systems and explore the required steps to successfully crack a WPA/WPA2 using hashcat. Upon completion, you'll be able to secure passwords using hashcat.
Exploring SecOps Tools: SQL Injection Testing Using sqlmap
sqlmap is an open-source penetration testing tool used to help security professionals automate the detection and exploitation of SQL injection vulnerabilities in web applications. It fully supports a broad range of databases and six SQL injection techniques. Through this course, learn how sqlmap works with common databases and helps automate common SQL injection techniques. Explore common sqlmap use cases and how to access, download, and install sqlmap. Next, discover the program's dependencies, including its various Python libraries. Finally, learn how to use sqlmap and Burp for database enumeration and dumping and bypass admin logins using sqlmap and SQL injections techniques. Upon completion, you'll be able to use sqlmap for SQL injection testing.
Exploring SecOps Tools: Digital Forensic Collection with Autopsy
Autopsy is an open-source digital forensic platform that simplifies the deployment of many of the utilities and plugins found in The Sleuth Kit forensic toolkit. Autopsy provides an easy-to-use graphical interface for command line digital investigation analysis tools, and provides fast, thorough, and efficient hard drive investigation solutions. In this course, discover the Autopsy platform, including features like timeline analysis, keyword searching, email analysis, and registry analysis. Investigate Autopsy benefits, such as ease of use, extensibility, efficiency, and cost effectiveness. Then, download and install Autopsy to explore the general configuration options panel along with the video triage and law enforcement bundle add-on modules. Finally, create a new case, view case details and the data source summary, and practice the various ways to add a data source.
Exploring SecOps Tools: Using the Social-Engineer Toolkit
The Social-Engineer Toolkit (SET) is used by security professionals and penetration testers to perform advanced attacks and social engineering. The SET offers attack vectors that help carry out human-side penetration testing exercises. In this course, you'll explore the SET and its capabilities and features. You'll also explore SET attack vectors, including phishing, web, infectious media generator, payload and listeners, and mass mailer attacks. Discover where to access installation files and how to install the SET. Learn how to start using the SET by launching the spear phishing module. Finally, explore how to perform web-based attacks, a credential harvester attack, and a man-in-the-middle attack.
SecOps Tools: The Role of AI in SecOps
Artificial intelligence, known commonly as AI, is the ability of a computer system to simulate human intelligence and carry out tasks that would otherwise require human intervention. Through this course, explore the benefits, history, and fundamentals of AI. Learn common AI applications and principles for AI that is protective of our privacy, unbiased, and socially beneficial. Discover common security threats facing AI and how AI can be exploited for malicious purposes. Explore different AI SecOps tools like Sophos Intercept X, IBM's QRadar Advisor, and Darktrace Antigena. Lastly, review common machine learning frameworks and tools that can be leveraged to build custom AI solutions. After completing this course, you will gain a better understanding of the importance of AI and the role it plays in security operations.
Building a SecOps Toolbox
Building a SecOps Toolbox
Final Exam: SecOps Tools Proficiency
Final Exam: SecOps Tools Proficiency will test your knowledge and application of the topics presented throughout the SecOps Tools Proficiency track.
Course options
We offer several optional training products to enhance your learning experience. If you are planning to use our training course in preperation for an official exam then whe highly recommend using these optional training products to ensure an optimal learning experience. Sometimes there is only a practice exam or/and practice lab available.
Optional practice exam (trial exam)
To supplement this training course you may add a special practice exam. This practice exam comprises a number of trial exams which are very similar to the real exam, both in terms of form and content. This is the ultimate way to test whether you are ready for the exam.
Optional practice lab
To supplement this training course you may add a special practice lab. You perform the tasks on real hardware and/or software applicable to your Lab. The labs are fully hosted in our cloud. The only thing you need to use our practice labs is a web browser. In the LiveLab environment you will find exercises which you can start immediately. The lab enviromentconsist of complete networks containing for example, clients, servers,etc. This is the ultimate way to gain extensive hands-on experience.
Sign In
WHY_ICTTRAININGEN
Via ons opleidingsconcept bespaar je tot 80% op trainingen
Start met leren wanneer je wilt. Je bepaalt zelf het gewenste tempo
Spar met medecursisten en profileer je als autoriteit in je vakgebied.
Ontvang na succesvolle afronding van je cursus het officiële certificaat van deelname van Icttrainingen.nl
Krijg inzicht in uitgebreide voortgangsinformatie van jezelf of je medewerkers
Kennis opdoen met interactieve e-learning en uitgebreide praktijkopdrachten door gecertificeerde docenten
Orderproces
Once we have processed your order and payment, we will give you access to your courses. If you still have any questions about our ordering process, please refer to the button below.
read more about the order process
Een zakelijk account aanmaken
Wanneer u besteld namens uw bedrijf doet u er goed aan om aan zakelijk account bij ons aan te maken. Tijdens het registratieproces kunt u hiervoor kiezen. U heeft vervolgens de mogelijkheden om de bedrijfsgegevens in te voeren, een referentie en een afwijkend factuuradres toe te voegen.
Betaalmogelijkheden
U heeft bij ons diverse betaalmogelijkheden. Bij alle betaalopties ontvangt u sowieso een factuur na de bestelling. Gaat uw werkgever betalen, dan kiest u voor betaling per factuur.

Cursisten aanmaken
Als u een zakelijk account heeft aangemaakt dan heeft u de optie om cursisten/medewerkers aan te maken onder uw account. Als u dus meerdere trainingen koopt, kunt u cursisten aanmaken en deze vervolgens uitdelen aan uw collega’s. De cursisten krijgen een e-mail met inloggegevens wanneer zij worden aangemaakt en wanneer zij een training hebben gekregen.
Voortgangsinformatie
Met een zakelijk account bent u automatisch beheerder van uw organisatie en kunt u naast cursisten ook managers aanmaken. Beheerders en managers kunnen tevens voortgang inzien van alle cursisten binnen uw organisatie.
What is included?
| Certificate of participation | Yes |
| Monitor Progress | Yes |
| Award Winning E-learning | Yes |
| Mobile ready | Yes |
| Sharing knowledge | Unlimited access to our IT professionals community |
| Study advice | Our consultants are here for you to advice about your study career and options |
| Study materials | Certified teachers with in depth knowledge about the subject. |
| Service | World's best service |
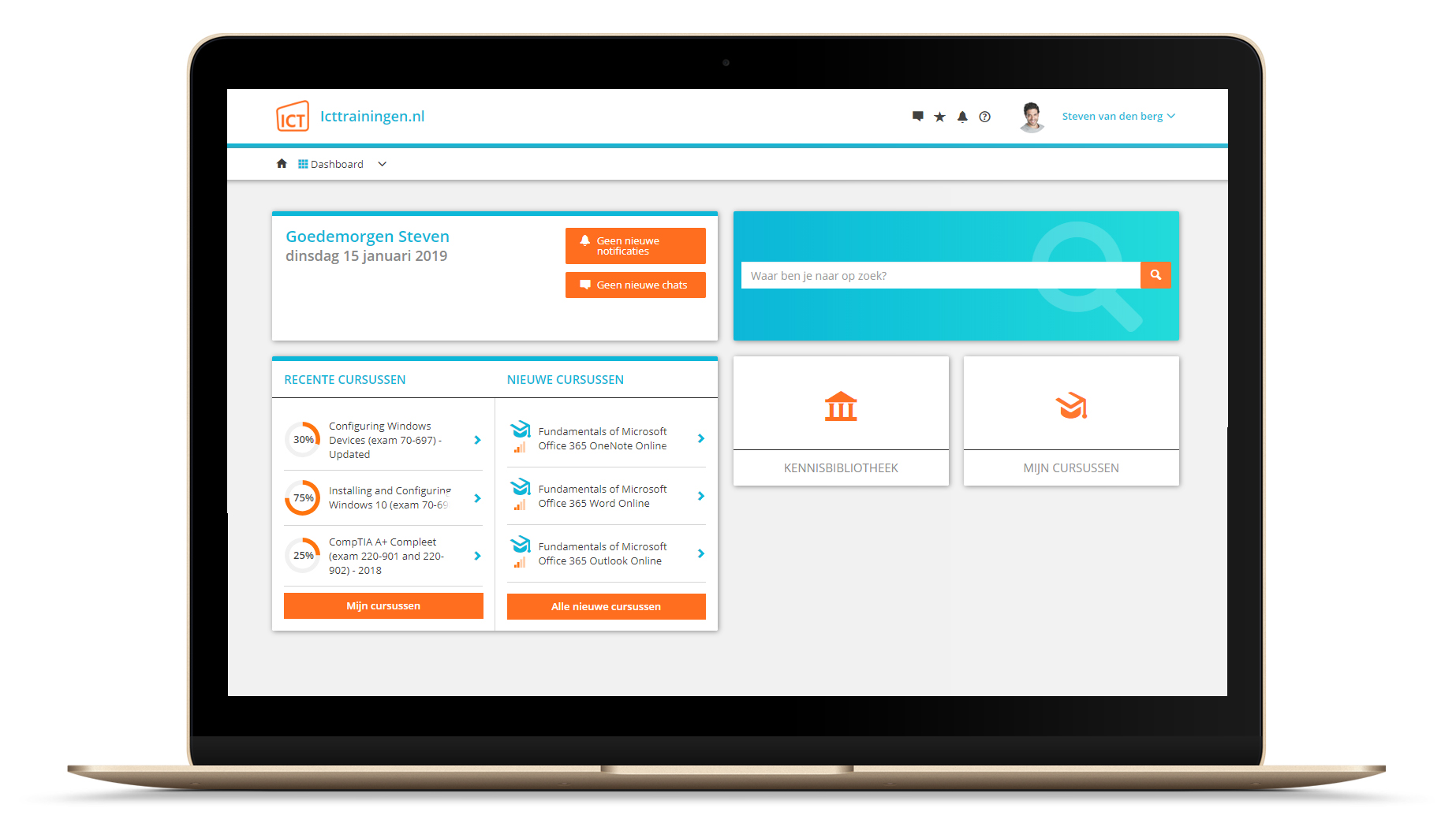
Platform
Na bestelling van je training krijg je toegang tot ons innovatieve leerplatform. Hier vind je al je gekochte (of gevolgde) trainingen, kan je eventueel cursisten aanmaken en krijg je toegang tot uitgebreide voortgangsinformatie.
FAQ
Niet gevonden wat je zocht? Bekijk alle vragen of neem contact op.