Course: Understanding Cisco Cybersecurity Operations Fundamentals (CCNP- CBROPS 200-201)
As low as
duration: 21 hours |
Language: English (US) |
access duration: 180 days |

Details
For those aspiring or current IT professionals pursuing a job role as an entry or associate-level cybersecurity analyst, or for those pursuing the Cisco Certified CyberOps Associate certification, this course will introduce you to cybersecurity operations in a security operation center.
Learn the fundamental skills, techniques and technologies necessary to prevent and defend against cyber attacks.
This training gives you insight into the network infrastructure devices, operations and vulnerabilities of the Transmission Control Protocol / Internet Protocol (TCP / IP) protocol suite.
You will learn basic information about security concepts, common network applications and attacks, the Windows and Linux operating systems and the types of data used to investigate security incidents.
You will learn more about:
- CIA Triad, a model for implementing security on networks.
- Threat Actors, security & risk management
- How the CVSS helps and what information it provides to a cybersecurity data analyst.
- Basics of the tcpdump and NetFlow tools.
- Data & Attack Types.
- Identifying various types of DOS, MITM and DDoS attacks.
- Techniques hackers use to evade detection.
- Different types of social engineer attacks.
- Recognizing resources within Linux.
- Malware analysis tools.
- The phase of the Cyber Kill Chain that can counter a phishing attack.
- How to extract files from a TCP stream from a PCAP file using Wireshark.
- The use of NIST SP 800-61 to identify forensic elements and how to apply them to the incident handling process.
And much more!
With this training, you prepare yourself for the CBROPS 200-201 exam. If you pass this exam, you will be in the process of obtaining the Cisco Certified CyberOps Associate certification.
Result
After completing this training, you will have the basic knowledge required to perform the associate-level cybersecurity analyst role, to strengthen network protocol, protect devices, and increase operational efficiency. You are also ready for the Cisco CBROPS 200-201 exam after following this training.
Prerequisites
There are no formal requirements for CyberOps Associate certification. It is advisable to have the following knowledge:
- Familiarity with Ethernet and TCP / IP networks.
- Practical knowledge of the Windows and Linux operating systems.
- Familiarity with the basics of network security concepts.
The CCNA training can helps you acquire the above knowledge.
Target audience
Network Administrator, Security Specialist
Content
Understanding Cisco Cybersecurity Operations Fundamentals (CCNP- CBROPS 200-201)
CBROPS: The CIA Triad & Security Approaches
For those aspiring or current IT professionals pursuing a job
- role as an entry or associate-level cybersecurity analyst, or for
- those pursuing the Cisco Certified CyberOps Associate
- certification, this course will introduce you to cybersecurity
- operations in a security operation center. You'll review security
- concepts, policies, and procedures used by a CyberOps Associate
- working within a SOC. You'll learn about the CIA triad, a model of
- implementing security on networks. Next, you'll explore basic
- models for cybersecurity and various security approaches. Finally,
- you'll review security terminology you should be familiar with and
- common security practices and tools for the CyberOps Associate.
- This course is one of a collection that prepares learners for the
- 200-201: Understanding Cisco Cybersecurity Operations Fundamentals
- (CBROPS) exam.
CBROPS: Threat Actors, Security, & Risk Management
In this course, you'll learn about threat actor types and review
- related examples. You'll then explore commonly confused security
- concepts - risk, threat, vulnerability, and exploit. Finally,
- you'll examine risk management concepts, including risk
- scoring/weighting, risk reduction, and risk assessment. This course
- is one of a collection that prepares learners for the 200-201:
- Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- exam.
CBROPS: CVSS, Deployments, Access Control, & Data Visibility
A SOC data analyst may depend on external data to help with
- understanding potential attacks against systems. In this course,
- you'll learn how the CVSS helps and what information it provides to
- a cybersecurity data analyst. You'll examine the implementation of
- security methods and how they fit into security design. You'll
- review how access control is implemented across an organization and
- some of the available access control models. Finally, it's
- important to know about network data visibility challenges, so
- you'll learn what they are and how to deal with them. This course
- is one of a collection that prepares learners for the 200-201:
- Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- exam.
CBROPS: Data Loss, Host Isolation, & Detection Methods
In this course, you'll learn to identify potential data loss
- indicators noted from a traffic profile. Then, you'll explore the
- 5-tuple approach for isolating a host. Finally, there are different
- detection methods that are used when securing networks dynamically.
- You'll review the similarities between them and how they operate to
- bring about usable results. This course is one of a collection that
- prepares learners for the 200-201: Understanding Cisco
- Cybersecurity Operations Fundamentals (CBROPS) exam.
CBROPS: Attack Surfaces, Vulnerability, & Analysis Tools
There are many things in cybersecurity that sound similar but
- are not. In this course, you'll learn to distinguish the attack
- surface from vulnerability. You'll also learn the basics of the
- tcpdump and NetFlow tools. This course is one of a collection that
- prepares learners for the 200-201: Understanding Cisco
- Cybersecurity Operation
CBROPS: Firewall, Filtering, Visibility, & Control Data
A key part of your role as an SOC data analyst is knowing what
- tool will give you the type of data type you want to analyze. In
- this course, you'll learn about useful next-gen and stateful
- firewall data. You'll explore content filtering, as well as web and
- e-mail content filtering, and why they are useful. Next, you'll
- review application level visibility and control data. Finally,
- you'll learn how the use of different technology can cause
- unexpected data visibility challenges. This course is one of a
- collection that prepares learners for the 200-201: Understanding
- Cisco Cybersecurity Operations Fundamentals (CBROPS) exam.
CBROPS: Data & Attack Types
In this course, you'll learn about data types that provide
- valuable information for security monitoring. You'll explore
- different network attacks, including protocol-based, DoS, DDoS and
- MITM attacks. Finally, you'll also look at common web application
- attacks like SQL injection, command injection, and cross-site
- scripting. This course is one of a collection that prepares
- learners for the 200-201: Understanding Cisco Cybersecurity
- Operations Fundamentals (CBROPS) exam.
CBROPS: Social Engineering, Evasion, Obfuscation, & Certificates
In this course, you'll examine multiple examples of social
- engineering attacks that you should be familiar with as an analyst.
- Attacks are not always easily identified, so you'll learn about the
- different evasion and obfuscation techniques. Finally, you'll learn
- about the different components of digital certificates and what
- these components do. This course is one of a collection that
- prepares learners for the 200-201: Understanding Cisco
- Cybersecurity Operations Fundamentals (CBROPS) exam.
CBROPS: Host-based Analysis & the Role of Attribution
In this course, you'll learn about host-based attacks in their
- various forms. Next, you'll explore components of Windows 10 and
- Ubuntu that are useful in host-based analysis. Finally, you'll
- examine the concept of attribution and its importance when
- investigating an organizational security breach. This course is one
- of a collection that prepares learners for the 200-201:
- Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- exam.
CBROPS: Log Evidence, Disk Images, & Malware Analysis Output
In this course, you'll examine the importance of logs, as well
- as types of evidence that can be acquired from them. Next, you'll
- learn how critical disk images can be during an investigation and
- about the comparisons and analysis that can transpire in an
- investigation. Finally, you'll review some of the most important
- information that can be found in the out of malware analysis tools.
- This course is one of a collection that prepares learners for the
- 200-201: Understanding Cisco Cybersecurity Operations Fundamentals
- (CBROPS) exam.
CBROPS: Security Events, Firewall Operations, & Traffic Analysis
In this course, you'll learn to categorize intrusion events
- according to the cyber kill chain and diamond intrusion models.
- Next, with so many tools available, you'll examine which ones
- should be used to identify different security events. You'll learn
- the differences between deep packet inspection, packet filtering,
- and stateful firewall operations. Finally, you'll review the
- differences between inline traffic interrogation, taps, and traffic
- monitoring. This course is one of a collection that prepares
- learners for the 200-201: Understanding Cisco Cybersecurity
- Operations Fundamentals (CBROPS) exam.
CBROPS: File Extraction, Event Artifacts, & Regular Expressions
In this course, you'll learn how to extract files from a TCP
- stream from a PCAP file using Wireshark. Next, you'll explore how
- to identify intrusion elements from a given pcap file using
- Wireshark. You'll learn how to interpret common artifacts from
- events for an alert using the Cisco FMC. Finally, you'll examine
- how to use basic regular expressions with grep and the Cisco CLI.
- This course is one of a collection that prepares learners for the
- 200-201: Understanding Cisco Cybersecurity Operations Fundamentals
- (CBROPS) exam.
CBROPS: Incident Response, Security Management, & Analysis
In this course, you'll review NIST800-86 to learn basic forensic
- techniques for incident response. You'll examine management
- concepts needed to be known and addressed in a security policy.
- Finally, you'll explore the relationship between metrics and scope
- analysis in a SOC. This course is one of a collection that prepares
- learners for the 200-201: Understanding Cisco Cybersecurity
- Operations Fundamentals (CBROPS) exam.
CBROPS: Protected Data, Profiling, Forensics, & IRP
In this course, you'll learn how to identify protected data in a
- network, as well as how to identify elements in network and server
- profiling. You'll explore the use of NIST SP 800-61 to identify
- forensic elements and how to apply them to the incident handling
- process. Finally, you'll learn how NIST SP 800-61 guides incident
- handling and review the elements of an incident response plan. This
- course is one of a collection that prepares learners for the
- 200-201: Understanding Cisco Cybersecurity Operations Fundamentals
- (CBROPS) exam.
Course options
We offer several optional training products to enhance your learning experience. If you are planning to use our training course in preperation for an official exam then whe highly recommend using these optional training products to ensure an optimal learning experience. Sometimes there is only a practice exam or/and practice lab available.
Optional practice exam (trial exam)
To supplement this training course you may add a special practice exam. This practice exam comprises a number of trial exams which are very similar to the real exam, both in terms of form and content. This is the ultimate way to test whether you are ready for the exam.
Optional practice lab
To supplement this training course you may add a special practice lab. You perform the tasks on real hardware and/or software applicable to your Lab. The labs are fully hosted in our cloud. The only thing you need to use our practice labs is a web browser. In the LiveLab environment you will find exercises which you can start immediately. The lab enviromentconsist of complete networks containing for example, clients, servers,etc. This is the ultimate way to gain extensive hands-on experience.
Sign In
WHY_ICTTRAININGEN
Via ons opleidingsconcept bespaar je tot 80% op trainingen
Start met leren wanneer je wilt. Je bepaalt zelf het gewenste tempo
Spar met medecursisten en profileer je als autoriteit in je vakgebied.
Ontvang na succesvolle afronding van je cursus het officiële certificaat van deelname van Icttrainingen.nl
Krijg inzicht in uitgebreide voortgangsinformatie van jezelf of je medewerkers
Kennis opdoen met interactieve e-learning en uitgebreide praktijkopdrachten door gecertificeerde docenten
Orderproces
Once we have processed your order and payment, we will give you access to your courses. If you still have any questions about our ordering process, please refer to the button below.
read more about the order process
Een zakelijk account aanmaken
Wanneer u besteld namens uw bedrijf doet u er goed aan om aan zakelijk account bij ons aan te maken. Tijdens het registratieproces kunt u hiervoor kiezen. U heeft vervolgens de mogelijkheden om de bedrijfsgegevens in te voeren, een referentie en een afwijkend factuuradres toe te voegen.
Betaalmogelijkheden
U heeft bij ons diverse betaalmogelijkheden. Bij alle betaalopties ontvangt u sowieso een factuur na de bestelling. Gaat uw werkgever betalen, dan kiest u voor betaling per factuur.

Cursisten aanmaken
Als u een zakelijk account heeft aangemaakt dan heeft u de optie om cursisten/medewerkers aan te maken onder uw account. Als u dus meerdere trainingen koopt, kunt u cursisten aanmaken en deze vervolgens uitdelen aan uw collega’s. De cursisten krijgen een e-mail met inloggegevens wanneer zij worden aangemaakt en wanneer zij een training hebben gekregen.
Voortgangsinformatie
Met een zakelijk account bent u automatisch beheerder van uw organisatie en kunt u naast cursisten ook managers aanmaken. Beheerders en managers kunnen tevens voortgang inzien van alle cursisten binnen uw organisatie.
What is included?
| Certificate of participation | Yes |
| Monitor Progress | Yes |
| Award Winning E-learning | Yes |
| Mobile ready | Yes |
| Sharing knowledge | Unlimited access to our IT professionals community |
| Study advice | Our consultants are here for you to advice about your study career and options |
| Study materials | Certified teachers with in depth knowledge about the subject. |
| Service | World's best service |
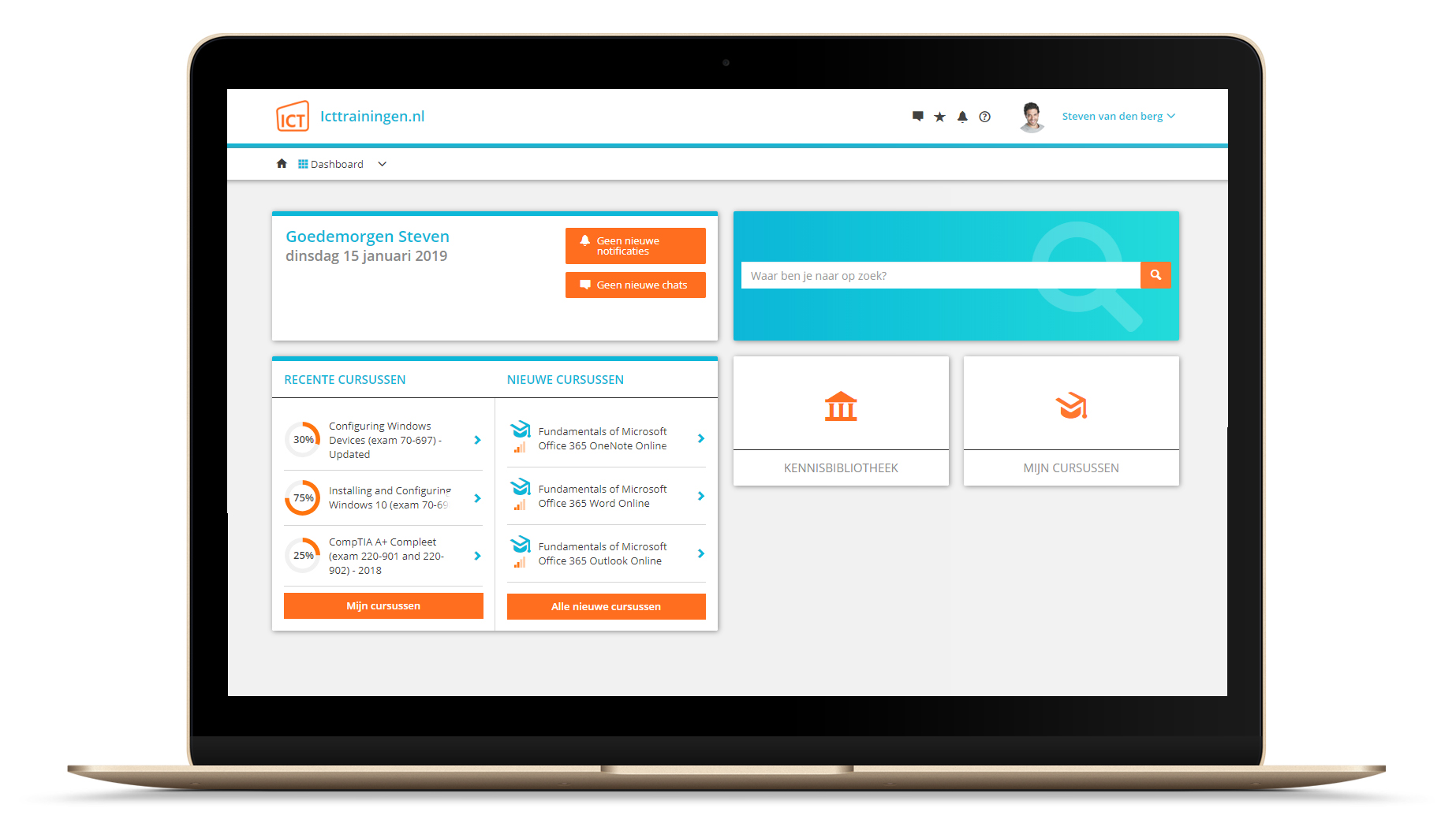
Platform
Na bestelling van je training krijg je toegang tot ons innovatieve leerplatform. Hier vind je al je gekochte (of gevolgde) trainingen, kan je eventueel cursisten aanmaken en krijg je toegang tot uitgebreide voortgangsinformatie.
FAQ
Niet gevonden wat je zocht? Bekijk alle vragen of neem contact op.