Course: Getting Started with Information Security
duration: 14 hours |
Language: English (US) |
access duration: 90 days |

Details
Information Security (or "infosec") is term for all actions and programs used in countering digital threats. The purpose of Information Security is to protect digital information in order to prevent threats. In addition, minimizing damage in the event of a problem is also an important part.
In this training you will learn more about:
- Common APT attacks.
- Important features of network access control (NAC).
- Different types of IT governance frameworks.
- Using Metasploit framework in Kali Linux.
- Different types of DNS attacks.
- Use security protocols in different situations.
Result
After following this training you will be familiar with the important aspects of Information Security and you can get started.
Prerequisites
You have a great knowledge of computer systems.
Target audience
Security Specialist
Content
Getting Started with Information Security
Information Security: APT Defenses
In this 13-video course, discover key Advanced Persistent Threat
- (APT), concepts such as defense and best practices. Explore common
- APT attacks and mitigation techniques that can be used, APT tools,
- and how to create effective APT checklists. You will begin with an
- introduction to APT and its purpose, then look at the steps of the
- APT lifecycle. Learners will examine motives behind an APT and
- probable targets, and learn to identify APT defense best practices.
- Next, you will explore methods that can be used to strengthen APT
- defenses, and then recall the method(s) to deal with APTs. You will
- then take a look at the Equation aka APT group and its involvement
- in various cyber crimes. Another tutorial examines the key tools
- that are used when conducting an APT. Define risk assessment
- processes that can help you protect your assets. In the final
- tutorial in this course, you will be asked to identify key points
- for creating an effective checklist to address APT attacks.
Information Security: NACs & Gateways
Discover the key NAC concepts such as NAC features, the importance of NAC in a network, various NAC elements, authentication, and its implementation. Explore the risks and challenges associated with BYOD and IoT.
Information Security: Subnetting & DNS for Security Architects
Discover key concepts related to subnetting, VM, Container, and DNS security. Examine tips and tricks used in subnetting and subnetting advantages. Explore CIDR notation, deployment and security considerations for VMs and containers, and types of DNS attacks and mitigation strategies.
Information Security: Securing Networking Protocols
Explore the key concepts of common protocols in use, and discover the security issues of TCP/IP model and security protocols.
Information Security: Hardened Security Topologies
In this 8-video course, learners will discover the key concepts
- of different security topologies and the key role they play in
- network security. Begin with an introduction to security
- topologies, which define the network design based on security
- requirements. You will then explore the design goals for security
- topology, the elements used to ensure that the information is
- secure, which means that you need the concepts of confidentiality,
- integrity, and availability (CIA), of information in a proper way,
- and it needs to be secured. You also need to practice
- accountability along with CIA concepts. Next, you will examine
- advantages and disadvantages of different security topologies,
- which are the Intranet, the Internet, and various other topologies.
- You will take a look at the impact of integrating cloud topologies,
- and also delve into the various layers of security in cloud
- computing. The final tutorial in this course explores the different
- methods used to harden the components of security topologies.
Information Security: Continual Infrastructure Testing
Discover key DevOps concepts such as continuous security and security monitoring, benefits of using DevOps and best practices of DevOps security. Explore the secure DevOps lifecycle and learn about security risks and the various tools used for DevOps testing.
Information Security: Security Governance
Discover the importance of implementing security governance in
- an organization. Explore the differences between governance and
- management, types of governance frameworks, and the roles of senior
- management. Ensuring good IT security governance, risks and
- opportunities, security governance programs, and governance
- framework structure is also covered.
Information Security: Honeypots
Explore various honeypot concepts, such as the types of
- honeypots, roles and uses of a honeypot, and how honeypot data
- analysis is used. In this 12-video course, you will examine
- strengths and weaknesses of a honeypot and how it is placed in
- networks. Key concepts covered in this course include the honeypot
- system itself, configured to detect, deflect, or counteract any
- unauthorized attempt to gain access to information; learning the
- various types of honeypots that can be used focusing on low and
- high interaction level types; and learning about the role played by
- honeypots in overall network security. Next, you will examine learn
- honeypot uses and disadvantages; learn the deployment strategies of
- a honeypot; and learn the various open-source and commercial
- honeypot products available on the market. Finally, learners will
- observe how honeypots are placed in a network; how to install and
- configure a honeypot by using KFSensor honeypot software; and
- explore how honeypot data analysis is captured through automated
- software or through a manual method.
Information Security: Pen Testing
Explorer the key pen testing concepts such as vulnerability assessment, types of pen testing, and threat actors. Discover why pen testing is needed and the tools used for pen testing.
Course options
We offer several optional training products to enhance your learning experience. If you are planning to use our training course in preperation for an official exam then whe highly recommend using these optional training products to ensure an optimal learning experience. Sometimes there is only a practice exam or/and practice lab available.
Optional practice exam (trial exam)
To supplement this training course you may add a special practice exam. This practice exam comprises a number of trial exams which are very similar to the real exam, both in terms of form and content. This is the ultimate way to test whether you are ready for the exam.
Optional practice lab
To supplement this training course you may add a special practice lab. You perform the tasks on real hardware and/or software applicable to your Lab. The labs are fully hosted in our cloud. The only thing you need to use our practice labs is a web browser. In the LiveLab environment you will find exercises which you can start immediately. The lab enviromentconsist of complete networks containing for example, clients, servers,etc. This is the ultimate way to gain extensive hands-on experience.
Sign In
WHY_ICTTRAININGEN
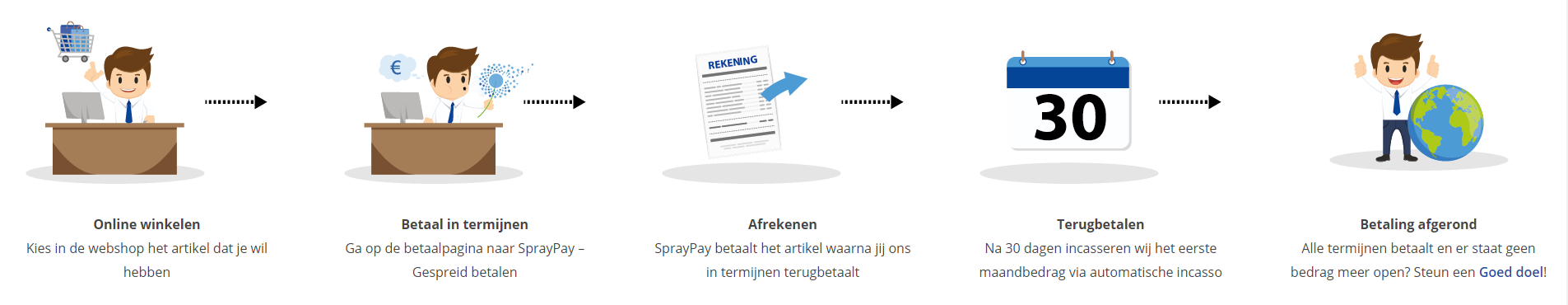
Via ons opleidingsconcept bespaar je tot 80% op trainingen
Start met leren wanneer je wilt. Je bepaalt zelf het gewenste tempo
Spar met medecursisten en profileer je als autoriteit in je vakgebied.
Ontvang na succesvolle afronding van je cursus het officiële certificaat van deelname van Icttrainingen.nl
Krijg inzicht in uitgebreide voortgangsinformatie van jezelf of je medewerkers
Kennis opdoen met interactieve e-learning en uitgebreide praktijkopdrachten door gecertificeerde docenten
Orderproces
Once we have processed your order and payment, we will give you access to your courses. If you still have any questions about our ordering process, please refer to the button below.
read more about the order process
Een zakelijk account aanmaken
Wanneer u besteld namens uw bedrijf doet u er goed aan om aan zakelijk account bij ons aan te maken. Tijdens het registratieproces kunt u hiervoor kiezen. U heeft vervolgens de mogelijkheden om de bedrijfsgegevens in te voeren, een referentie en een afwijkend factuuradres toe te voegen.
Betaalmogelijkheden
U heeft bij ons diverse betaalmogelijkheden. Bij alle betaalopties ontvangt u sowieso een factuur na de bestelling. Gaat uw werkgever betalen, dan kiest u voor betaling per factuur.

Cursisten aanmaken
Als u een zakelijk account heeft aangemaakt dan heeft u de optie om cursisten/medewerkers aan te maken onder uw account. Als u dus meerdere trainingen koopt, kunt u cursisten aanmaken en deze vervolgens uitdelen aan uw collega’s. De cursisten krijgen een e-mail met inloggegevens wanneer zij worden aangemaakt en wanneer zij een training hebben gekregen.
Voortgangsinformatie
Met een zakelijk account bent u automatisch beheerder van uw organisatie en kunt u naast cursisten ook managers aanmaken. Beheerders en managers kunnen tevens voortgang inzien van alle cursisten binnen uw organisatie.
What is included?
| Certificate of participation | Yes |
| Monitor Progress | Yes |
| Award Winning E-learning | Yes |
| Mobile ready | Yes |
| Sharing knowledge | Unlimited access to our IT professionals community |
| Study advice | Our consultants are here for you to advice about your study career and options |
| Study materials | Certified teachers with in depth knowledge about the subject. |
| Service | World's best service |
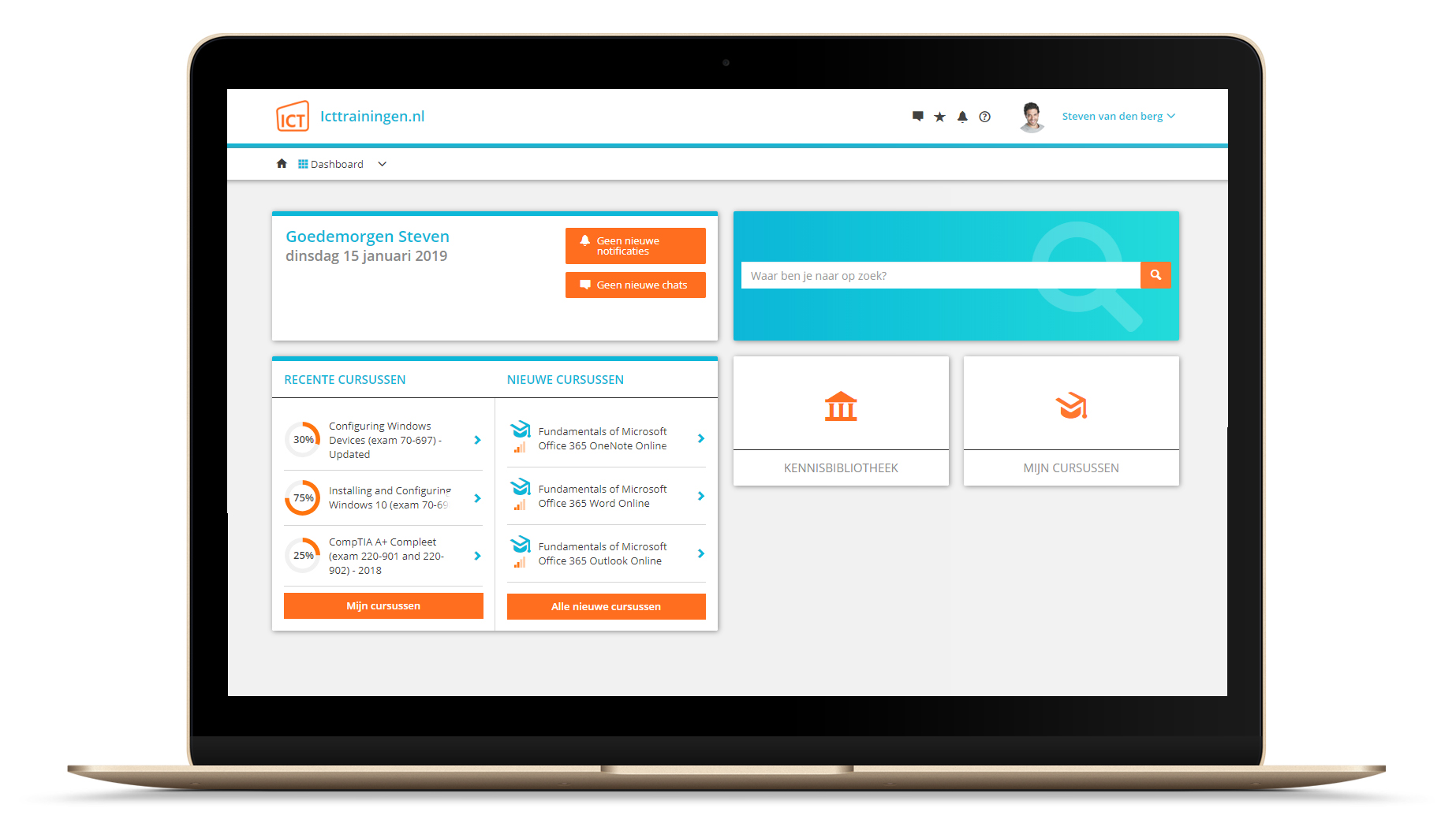
Platform
Na bestelling van je training krijg je toegang tot ons innovatieve leerplatform. Hier vind je al je gekochte (of gevolgde) trainingen, kan je eventueel cursisten aanmaken en krijg je toegang tot uitgebreide voortgangsinformatie.
FAQ
Niet gevonden wat je zocht? Bekijk alle vragen of neem contact op.